 Once a year, as every SAP administrator and security manager knows, the annual external audit is a given. Despite this, the current risk situation of the SAP systems is often uncertain. Have all the vulnerabilities from the last audit really been taken care of? Have new risks arisen in the meantime? If you don’t take active countermeasures, you might end up in the same situation again and again.
Once a year, as every SAP administrator and security manager knows, the annual external audit is a given. Despite this, the current risk situation of the SAP systems is often uncertain. Have all the vulnerabilities from the last audit really been taken care of? Have new risks arisen in the meantime? If you don’t take active countermeasures, you might end up in the same situation again and again.
The next audit is always right around the corner
SAP authorization concepts are subject to continual change, which is why auditors check every year to make sure that authorizations like SAP_ALL and the SAP standard users are protected, along with examining SoD risks. The list of necessary measures is long: from installing security patches to checking and reducing critical authorizations. Security specialists then often get the short-term order of ensuring that the list of findings from the previous year’s external audit has been processed thoroughly and that no serious risks have arisen in the meantime – whether debug and replace, deletion of change documents, or starting all reports that involve individual critical authorizations. One reason for these ad hoc orders: there has been no follow-up of the cleanups from the previous audit due to a lack of resources.
If you limit yourself to this reactive approach, you’re bound to go through the same cycle over and over again.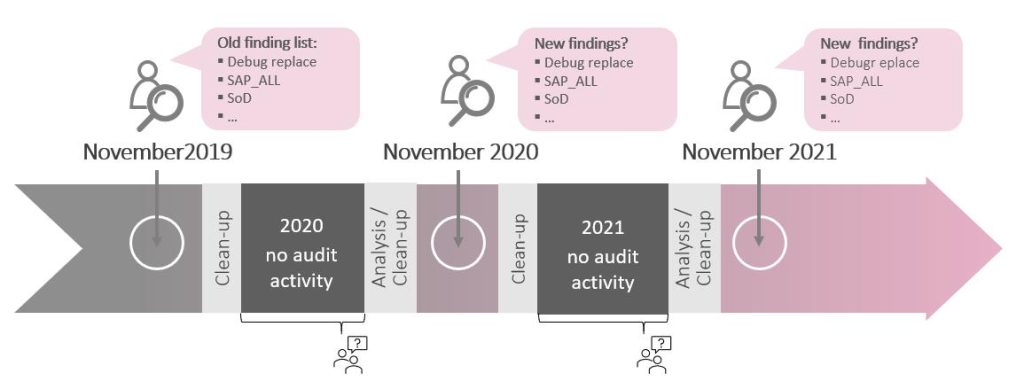
If the previous findings are eliminated or mitigated just before the next audit, the auditor doesn’t test for them alone; they run additional tests as well, of course, and produce a new list of findings – and the game starts all over again. Although this snapshot-based approach is essential to avoiding short-term damage, it is not a viable future strategy. The compliance status of the system deteriorates immediately whenever new authorizations are assigned; this creep cannot be prevented proactively. New risks often remain undetected over the year, at least until the next audit comes around. The end effect: There is no work aimed at continuous improvement of the situation, nor any ongoing risk monitoring.
Every external audit is merely a snapshot
A list of findings only reveals a small sample of the risks in an SAP system. But what about analyses of transactions, changes, and system behavior? When and where have employees deviated from the specified working methods? Were differing settings intentionally changed back to the “target” state? Still, the solution to this problem is relatively simple: Don’t wait until the next audit! Instead, identify your vulnerabilities today. It’s the only way to guarantee the security of your SAP systems year-round and enable you to react to anomalies quickly.
Proactive risk management is better than reactive
The easiest, most thorough way to achieve this is by using an end-to-end, tool-supported solution for SAP threat detection and access governance – like the SAST SUITE. It not only provides extensive real-time monitoring, but also facilitates the integration of cyclical checks, even up to producing an audit plan with a dedicated policy for the auditor’s list of findings. As a result, regular internal audits are used in addition to annual review by external auditors, to check the configuration of SAP landscapes and user authorizations. Their benefits: They analyze individual aspects of the system in shorter time intervals, help with preparation for and follow-up to the annual audits, and support internal control systems.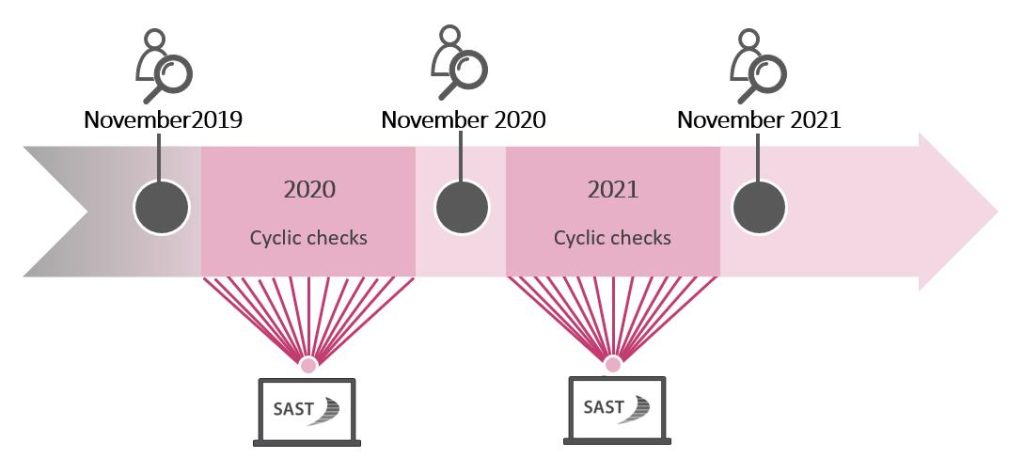
Take an end-to-end approach
The SAST SUITE enables fast, effective ad hoc cleanup of the external auditor’s findings. Initial activities like this should remain the exception, however, and only represent the starting point, to prevent any gaps in monitoring over time. A reliable IT security concept requires a solution like the SAST SUITE – one that enables proactive risk management and helps you reach a continuous “stay clean” stage through regular analyses and cyclical checks, with a clear audit plan, definition of the audit scope, planning of recurring checks, and automated audit execution. All these factors will help to ensure that cleaned systems stay clean, so you’ll never have to dread an auditor visit again.
For more information, visit our SAST SOLUTIONS website or just get in touch.
Further articles on the topic:
Knock, knock! What if a hacker has already broken in when your IT auditor is at the door?
How to plan and carry out your SAP System Audit with SAST Risk and Compliance Management

