 The procedure is well-known at SMEs and large companies: Every year, the auditor comes around for the IT audit, which is carried out as part of the annual overall review. The general objective is to ensure the security and integrity of the audited system (usually the SAP system used for accounting) and to identify potential risks. A management letter then describes follow-up measures to mitigate these risks in future. But does this approach still make sense today?
The procedure is well-known at SMEs and large companies: Every year, the auditor comes around for the IT audit, which is carried out as part of the annual overall review. The general objective is to ensure the security and integrity of the audited system (usually the SAP system used for accounting) and to identify potential risks. A management letter then describes follow-up measures to mitigate these risks in future. But does this approach still make sense today?
An IT audit is a snapshot. What you need is real-time monitoring.
If we ask ourselves whether the audit checks can actually get to the root of the risks and identify and handle them quickly, we realize that this can only be a supplementary measure. It is not a solution-oriented method from the risk perspective, particularly in fast-moving IT landscapes.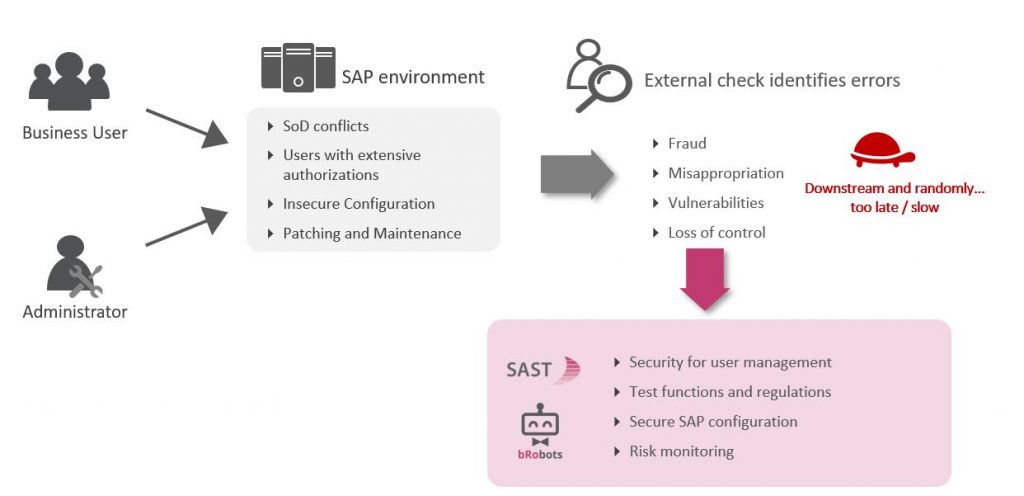
A better, more contemporary approach is “360-degree real-time monitoring” – identifying risks and presenting them transparently in the event that they actually occur. The SAST SUITE and its Security Radar meets these requirements. Instead of a one-time, sample-based test whose result is statistically relevant for the general population, the solution implements event-driven real-time monitoring of the SAP system, to identify occurring events directly and implement the necessary subsequent steps.
SAST helps you find the needle in the haystack.
The SAST Security Radar has out-of-the-box data sources and events that are monitored continuously. If an event occurs, a follow-up task is initiated immediately. This could involve notifying the security officer, for example, as well as blocking a download in process.
The events described as examples below emphasize the possibilities for mitigating the resulting risks immediately:
- The SAP system was opened > Immediate notification
- Critical data/prices are downloaded from tables > Block the download process > Notification/approval
- A user is assigned a critical profile (such as SAP_ALL) > Immediate notification
- The critical transaction XYZ was called with user ID ABC > Immediate notification
- A user assigns roles to their own SAP user > Immediate notification
AKQUINET business Robots as an enhancement to SAST Security Radar.
We have enhanced the SAST Security Radar-based approach from the compliance perspective with AKQUINET business Robots (bRobots), which make it possible to analyze specific business processes based on rules and making intelligent decisions whether to allow those processes to advance:
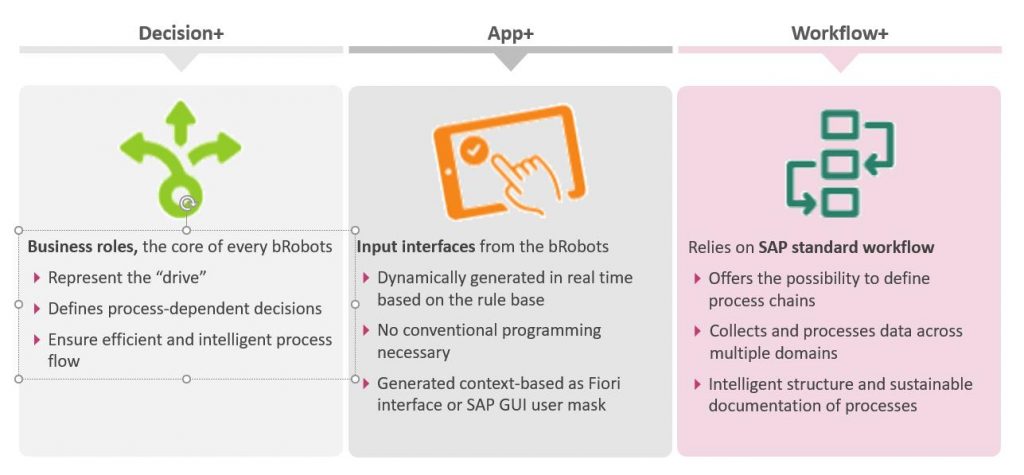
If fields defined as “critical” are changed, for example (such as a supplier’s bank data, prices, inventory levels, and so on), “Decision+” from bRobots recognizes this and triggers a workflow (Workflow+). This enables us to integrate the dual-control principal dynamically and obtain approval for the change via “App+”:
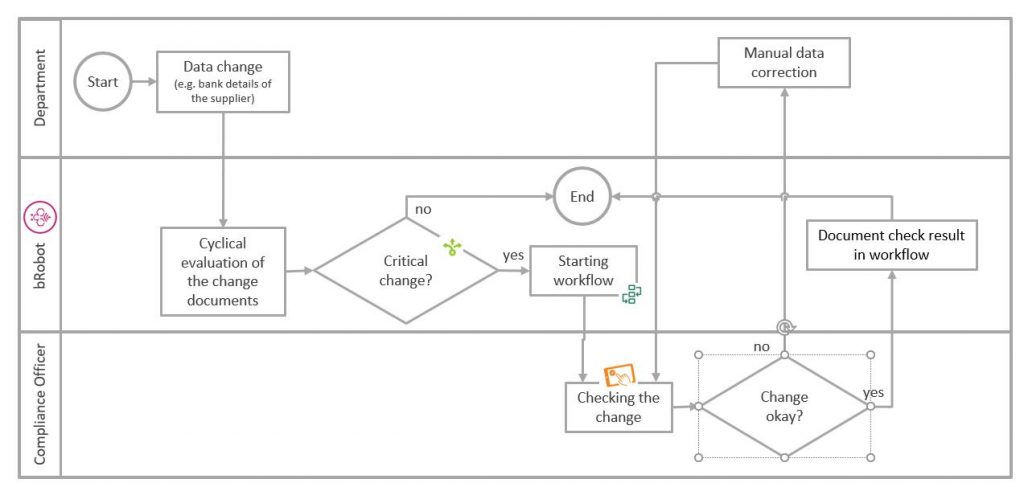
The result is an intelligent, rule-based control system without rigid, cost-intensive and resource-intensive workflows with fixed dual-control principles.
In a second use case, we focus on critical changes to prices:
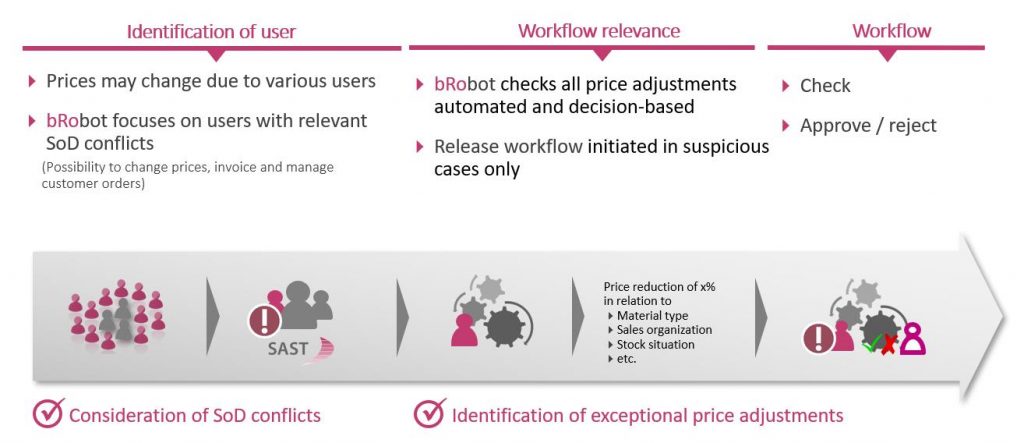
When users who theoretically have a separation-of-duties conflict change prices beyond a certain percentage, dependent on other decision-making parameters (such as the material type), the bRobot triggers a workflow dynamically and waits to implement the price change in the system until it has been reviewed and approved.
Combining SAST Security Radar and business Robots (bRobots) makes it possible to identify critical events in the security and compliance concept dynamically and intelligently, make them transparent, and initiate relevant follow-up steps.
Tip: You gain get deeper insights into this topic in the webinar of the same name: “What if a hacker has already broken in when your IT auditor is at the door? How to actually protect your SAP systems.” Simply request the link to the recording to find out more – preferably before your next audit.

Michael Müllner (Head of Security & Compliance Services, AKQUINET Austria)
This could also interest you:
The importance of reliably monitoring transactions in SAP systems
SAP home goes rogue – preventable attack vectors through the SAP GUI


