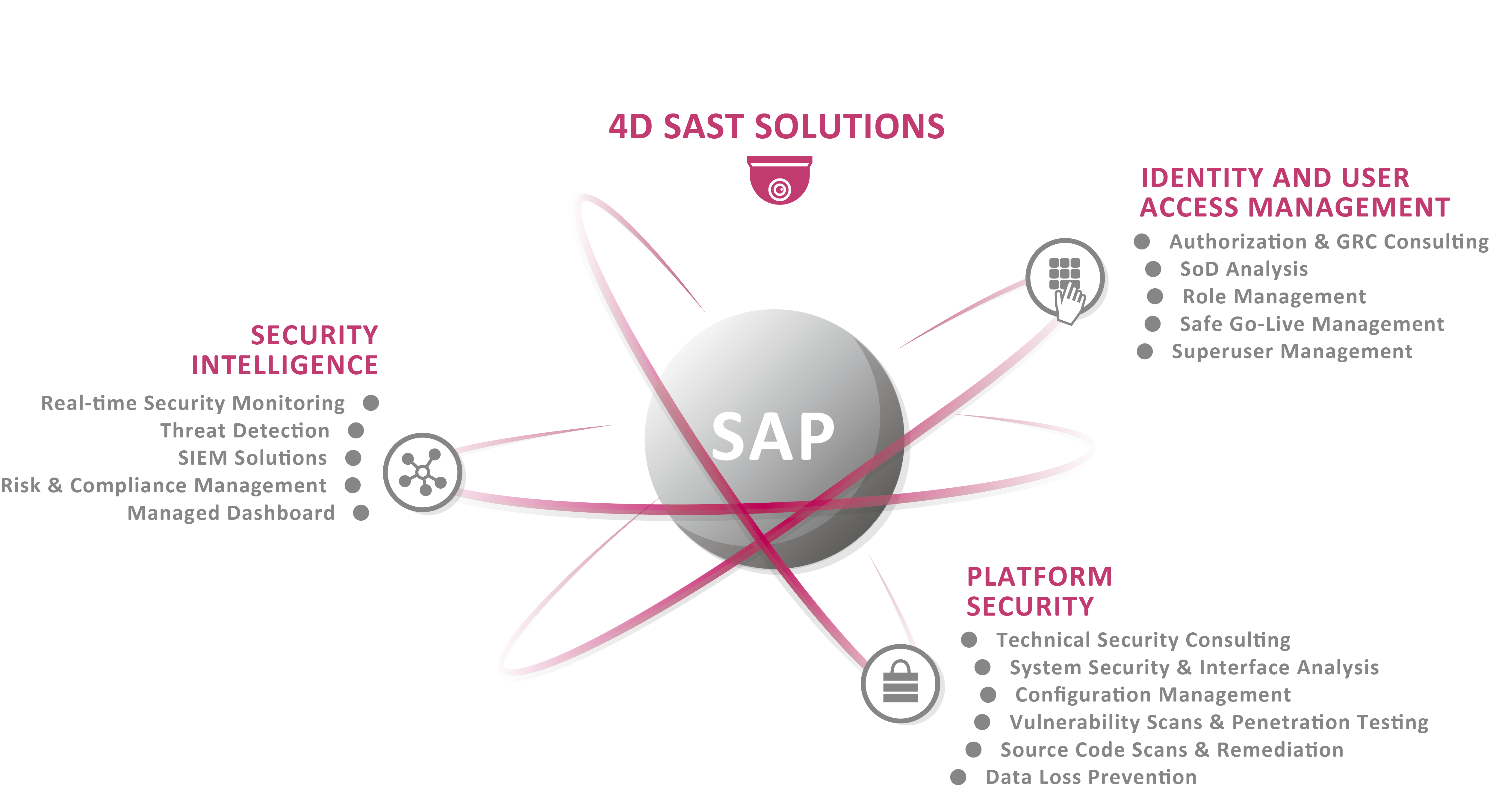
“With the help of the SAST SUITE, we were able to significantly reduce the probability of occurrence for critical events.
And thanks to the introduction of the Security Dashboard, the visibility of these incidents is now considerably better than before.
As a result, we are now in a position where we can respond much faster to critical events.”
Success Story "Global SAP security with real-time monitoring"
Success Story "SAP risk management with managed Services"