 Sensitive enterprise data demands special protection. In addition to company-specific protection requirements, industry-specific specifications and legal regulations must also be observed. Minimizing the risk of losing critical data from SAP systems requires a variety of coordinated measures, collectively known as “data loss prevention”.
Sensitive enterprise data demands special protection. In addition to company-specific protection requirements, industry-specific specifications and legal regulations must also be observed. Minimizing the risk of losing critical data from SAP systems requires a variety of coordinated measures, collectively known as “data loss prevention”.
Downloads pose a particular risk and should be monitored
In a standard SAP ERP or SAP S/4HANA system, particularly in production environments, users usually don’t need direct table access. Key users are an exception to this, because they need to change current settings, such as the FI posting periods. SAP already provides appropriate transactions for such tasks in the standard system, enabling you to avoid granting generic access. In practice, however, we have noticed that these users receive extensive authorizations, particularly to start downloads. Downloads present a potentially critical risk in general and should therefore be logged in the SAP system. The criticality of downloads is enterprise-specific and can be determined based on their source, size, frequency, and other criteria.
We offer a smart, reliable solution for identifying critical downloads:
Data Loss Prevention with our SAST SUITE
The SAST SUITE enables you to identify potential incidents quickly and protect yourself against data loss. As soon as a user starts a download from a critical transaction, the process is logged and the software generates an event.
The following example illustrates a download of the user table USR02 with the password hash values from transaction SE16.
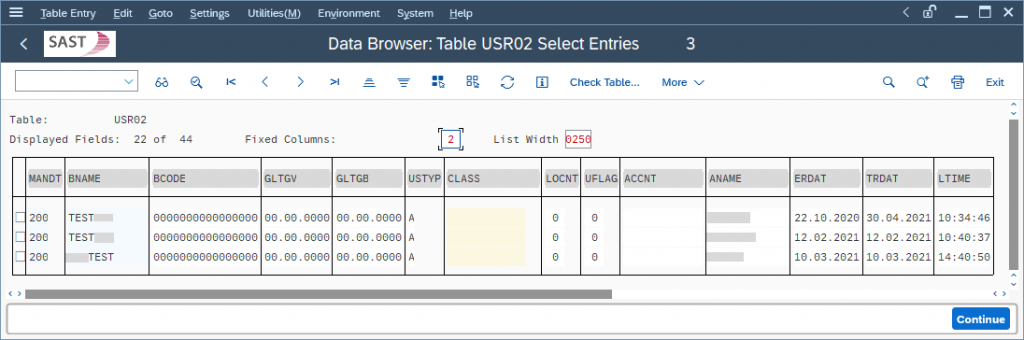
When the download is started from transaction SE16 using the function “Save as Local File”, the user sees the following logging message:
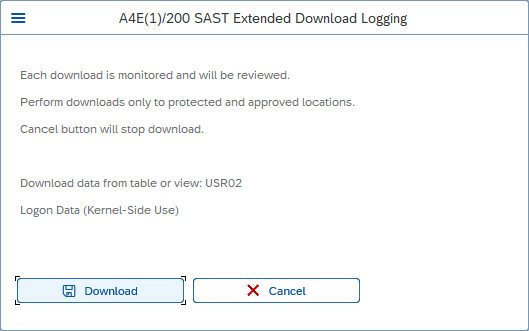
When “Download” is clicked, the table contents are saved on a local drive and the download is logged as described in the message. The SAST SUITE analyzes the log and triggers the appropriate events.
In addition to the table name, the event view also displays information about the transaction and the terminal used, along with a time stamp and the size of the saved file.
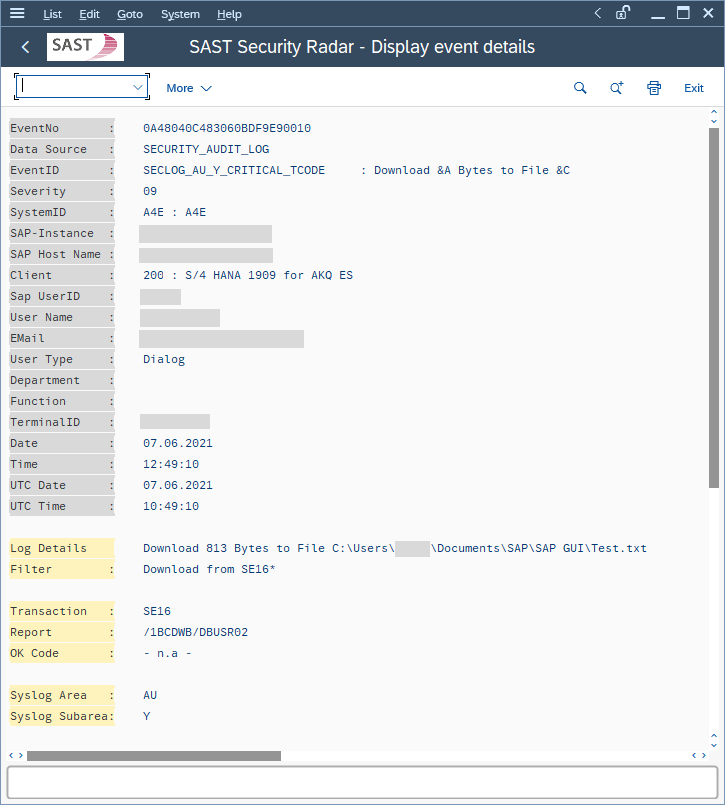
Based on this information, IT administrators can now identify download attempts and – particularly when critical data is downloaded – approach the user and ask whether these downloads are really necessary, as well as track the status of the data.
Get the security status of your entire SAP system landscape at the touch of a button!
The SAST SUITE lets you define specific critical transactions yourself in just a few simple steps and get alerts in the case of complex events – even as combinations of multiple incidents that aren’t critical on their own. You will be able to identify future risks in real time and display a graded, dashboard-based display of your security status at the touch of a button.
We will be happy to support you in designing data loss prevention measures at your company. For more information, visit our website or send us an e-mail.

Viktor Vogt (SAP Security Consultant, SAST SOLUTIONS)
More about security intelligence:
Security dashboards – Just a buzzword or a true help with the daily security routine?

