 Standard SIEM monitoring is often insufficient to ensure SAP security, because the specific SAP logs and analyses can’t be interpreted and, consequently, attack patterns cannot be identified or recognized. Why this is the case, what companies can do to integrate SAP in their monitoring nonetheless, and why this end-to-end safeguarding can deliver additional benefits – our CTO Ralf Kempf explains it all in an article for it management magazine.
Standard SIEM monitoring is often insufficient to ensure SAP security, because the specific SAP logs and analyses can’t be interpreted and, consequently, attack patterns cannot be identified or recognized. Why this is the case, what companies can do to integrate SAP in their monitoring nonetheless, and why this end-to-end safeguarding can deliver additional benefits – our CTO Ralf Kempf explains it all in an article for it management magazine.
SIEM (Security Information and Event Management) serves to safeguard the security of IT environments for companies and organizations. It combines Security Information Management (SIM) with Security Event Management (SEM) to generate real-time analyses of security alerts. The collection, correlation, and analysis of log data, system messages, and alerts make it possible to identify attacks, unusual patterns, and dangerous trends. As such, SIEM provides an overview of security-relevant events in IT environments, helping to meet legal requirements and satisfy internal policies and compliance rules for IT security. The key tasks: provide reports on security-relevant incidents, such as successful and failed logon attempts, as well as malware and other potentially harmful activities, and send notifications when an analysis finds that an activity violates the defined rule sets and is therefore indicative of a potential security problem.
How SIEM works
When data is consolidated in one place, critical activities can be identified early on through analysis patterns and trends. The data is collected and interpreted in real time and the information gained is saved in unalterable form. Commonplace sources for SIEM include servers, firewalls, routers, IPS, and IDS. Their data is forwarded to a central point, where it is saved, normalized, structured, and analyzed for storage. The analyses use defined rules, correlation models, machine learning, and artificial intelligence to generate relations between the entries and identify anomalies. In contrast to other security measures, attacks are not prevented in advance, but its impact and spread can be reduced through alerts, for example. In addition, such alerts and automated reports enable responses to a variety of threats in real time, as well as subsequent documentation of security incidents. Unfortunately, this principle is hardly effective in SAP systems.
Parallel worlds: SAP and SIEM
There are a number of reasons why SIEM and SAP have misunderstood each other essentially from the outset: SIEM originates from classic network technology, for example, from an era under DOS and Ethernet with large, standalone mainframe applications for financial and managerial accounting, controlling, and more, all independent of one another. As the world of IT became more interconnected, SIEM was introduced to monitor happenings in the network layer – questioning where information originated from, who accesses it, what is already known, and what doesn’t fit established patterns. In this approach, rule sets are crucial: they are used to check occurrences in the network and draw conclusions for security. As such, classic SIEM tools consider IT infrastructures, not individual applications. In recent years, however, it has become increasingly apparent that applications also have to be included, whether Microsoft Dynamics, a product planning tool, or an SPS in production. This is followed by a big ‘but’ where SAP is involved: SAP is much different from other applications and essentially a network of its own. I can do many different things with SAP, both with roles and authorizations and with regard to security. While many of the mechanisms are similar to others in IT, SAP already differs with regard to its nomenclature and rule sets. As such, when it comes to network equipment and the rest of IT, SAP is virtually its own strange world, with its own language and diction. That’s why many companies still draw a line between SAP and their other IT.
SAP is ignored by SIEM – but it doesn’t have to be
Conventional SIEM tools concentrate on identifying unusual behavior within infrastructures. But SAP systems are often ignored. If no access is provided to the SAP system, SIEM can identify little more than a kind of ambient noise of logs with millions of entries that hardly anyone can interpret in the end – or even wants to. In other words: SAP systems represent a blind spot for most SIEM tools because they don’t include SAP-specific checking rules. This means they don’t recognize corresponding attack patterns, which is why security teams fail to identify certain threats and incursions. Exceptions in the SAP system may appear unremarkable at the network level. The only way to identify them is to consider the application itself. As a result of these problems of comprehension, many issues ignore SAP altogether, or tackle it last, because it’s easier to deal with things you understand, after all. That’s why SAP is often neglected: even companies that run highly professional IT security, use SIEM, and have gained a mastery of all non-SAP areas tend to ignore SAP, either unwittingly or even intentionally. Perhaps they hope that their SAP employees will somehow check things themselves or that the incomplete SIEM will be sufficient, or perhaps they aren’t even aware that there are possibilities for covering this deficit. CISOs at companies that use SIEM should ask themselves: am I certain that I am giving my SAP systems enough attention? If not, you should combine the two worlds, because it simply makes more sense to do so.
The best of both worlds
Since the network specialists have created efficient tools to provide an overview, but often forget that there are other worlds besides theirs, achieving true end-to-end protection means bringing both worlds together, for the benefit of the company. This is where software like the SAST SUITE comes in, which extracts events from the application layer and transports and translates them in a way that SIEM environments can understand. Detecting attacks based on log files and analyzing network traffic requires in-depth knowledge of the potential paths and patterns such incursions can follow. Intelligent information management is necessary in order to assess security data of this kind. Events relevant to security have to be filtered out of a sea of data and placed in the proper context.
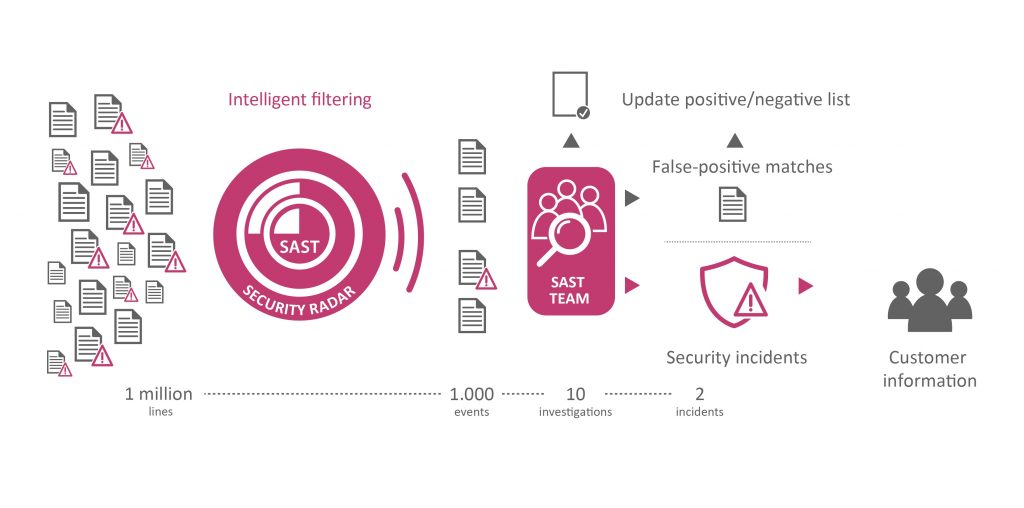
To identify risks, the SAST Security Radar not only analyzes SAP logs, but also integrates analyses of configurations and roles. The SAST SUITE features practically out-of-the-box functionality to feed this information from SAP to existing SIEM systems of all types, where it can be analyzed further. This works from small SAP systems to some of the world’s largest environments run by our customers, some with over 1,000 systems. A further benefit is the Security Dashboard: By integrating it with an overarching SIEM tool, you can consolidate all the security-relevant incidents detected in your SAP S/4HANA systems with other areas of your IT landscape. This ensures that SAP is taken into account in SIEM and companies can generate a reliable dashboard-based display of their full security status at the touch of a button.

Ralf Kempf (CTO SAST SOLUTIONS)
This article was originally published in it management magazine, July/August 2021 issue and is available free of charge from the online reader service on it-daily.net: https://www.it-daily.net/leser-service
This might also interest you:
The importance of reliably monitoring transactions in SAP systems

