 Companies that use SAP software, as well as the German-speaking SAP User Group (DSAG), are demanding security dashboards to provide for greater transparency and indicate necessary activities. The most critical risks, however, are those that arise as a combination of other events, which are not critical in and of themselves. After all, even the best dashboards aren’t able to display this kind of unidentified security incident.
Companies that use SAP software, as well as the German-speaking SAP User Group (DSAG), are demanding security dashboards to provide for greater transparency and indicate necessary activities. The most critical risks, however, are those that arise as a combination of other events, which are not critical in and of themselves. After all, even the best dashboards aren’t able to display this kind of unidentified security incident.
The following interview between Helge Sanden (Editor in Chief of IT-Onlinemagazin) and Ralf Kempf (CTO SAST SOLUTIONS) was published in IT-Onlinemagazin on March 2, 2021 (in German).
Mr. Kempf, what trends have you observed regarding vulnerabilities that can be exploited to attack SAP systems?
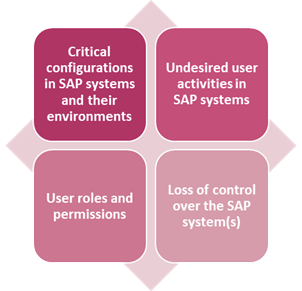
The much more interesting thing is that the major vulnerabilities of SAP systems have remained unchanged for years, but many companies haven’t fixed them yet. There’s incorrect system configuration, for one thing, which leaves too many loopholes for attackers to exploit. Then there’s the abuse of user roles and authorizations, and the third factor is unintended behavior by users in the system that results in internal security incidents.
What misconceptions about this do you see at companies?
Investments that companies successfully make in authorization and user management are often put at risk by the careless handling of the most fundamental security measures. In other words, companies have frequently made strides in authentication, user management, and authorizations, but they neglect two other crucial elements for comprehensive protection: The first is protecting the IT systems and the infrastructure itself; the second is a company-wide consolidation of all security settings through analyses and reports.
Many companies are still particularly undecided when it comes to implementing modern security dashboards for SAP landscapes. A popular cause of this seems to be apprehension about the effort needed, which contrasts with the decision-makers’ desire to achieve the greatest possible transparency and have an end-to-end overview in real time. But given the high efficiency of a security dashboard, these reservations are unwise and – in light of current threat levels – even dangerous. Using them delivers benefits for both effective real-time monitoring and the conservation of valuable internal IT resources.
And to continue to meet the challenges posed by the increasingly complex requirements of SAP security, dashboards are simply essential for a transparent overview. No company that runs SAP systems should miss out on these benefits because its nature as standard software means that the requirements for security, transparency, and monitoring are ultimately identical for everyone.
How can the detection rate for critical attacks be increased?
“Dashboard” has become a trendy buzzword in the interim and is often used far and wide to describe even products that merely combine static monitoring with a graphical user interface for the application. Products like this can hardly be adjusted or fine-tuned, however, even though the strength of a true end-to-end security dashboard is its very ability to adapt to unforeseen developments such as the current threat level.
A true security dashboard visualizes the information reflecting the diversity of the different systems and responsibilities for specific user groups, enabling a top-down perspective of the security and compliance standard currently achieved – all in real time. In addition, the solution not only has to show where such problems exist, but also provide recommendations for eliminating them.
Due to the particular complexity of the SAP systems in combination with the many internal company needs, the implementation of a security dashboard demands detailed knowledge of the internal processes and responsibilities of the persons responsible, including profound SAP security expertise. This is what is missing at many companies.
What characterizes a good security dashboard?
A security dashboard must make it possible to combine the data for each situation, regardless of its source, and to visualize reporting for the IT security department and for system owners.
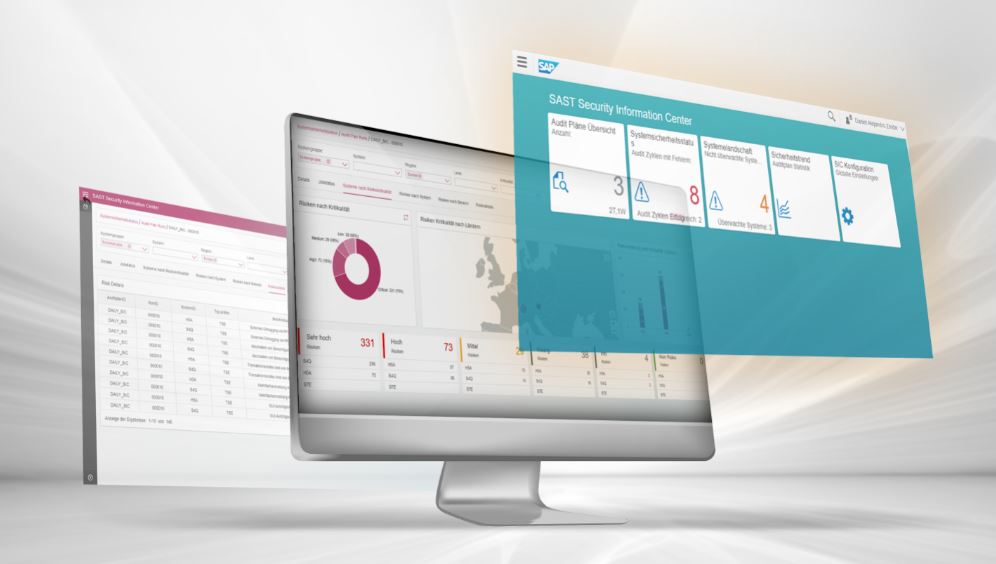
System owners, in particular, need a simple overview with just two traffic lights at the top level: One for the “configuration and authorizations” area and the other for “SIEM/real-time monitoring”. Through this approach, system owners know immediately where they have to take action and can retrieve details of the incidents and appropriate recommendations for action in real time.
Some SAP customers have to monitor the results of around 2,000 individual check processes from 300 SAP systems daily in practice to identify vulnerabilities caused by critical configurations and conspicuous user behavior. The only way to do this easily and in real time is with a security dashboard that lets you navigate through different levels, down to the details of a specific alert message.
Are there typical early warning signs of an attempted attack?
There aren’t any really “typical” early warning indicators, because the vulnerabilities and attack vectors are simply too diverse – and also change constantly.
But there are warning signals, of course, which too many companies unfortunately ignore. Negative results from a security audit come to mind, for example. It’s almost alarming how many companies are aware of certain vulnerabilities but have not eliminated them yet. Such findings often lie hidden in desk drawers. We lack a healthy culture of learning from our mistakes, where the only relevant points are creating transparency and bringing errors to light, and not concentrating on the misconduct of employees – which might not even be intentional.
Therefore, one of our most important recommendations always says, react immediately, assess vulnerabilities based on their criticality, and don’t procrastinate when it comes to correcting them. After all, time is the decisive factor when a relevant attack occurs.
What can you do if you identify an attack in progress?
Here, as well, there’s no patent remedy that cures all ills, because the best reaction is highly dependent on the respective attempted attack. But what all responses have in common is that they require a clearly organized risk management structure at the company, with defined processes on how to proceed through risk scenarios. The procedure models from ISO2700x, BSI, or NIST can help here, for example.
What will you be talking about at the IT online conference 2021?
In the SAST Expert Talk, Andreas Feistl from Linde will provide insights into his company’s SAP security strategy and show how integrating the SAST SUITE in their SIEM monitoring enables them to detect critical and complex SAP security incidents in real time.
In addition, we’ll talk about our day-to-day practices, for example, the requirements of a security information center and how dashboards can help to round out the continuous monitoring of SAP systems. After all, the important thing is to detect and assess incidents as quickly as possible, to introduce counter-measures with the least possible delay.
What do you expect the dominating topic in SAP security to be in 2021?
It’s quite noticeable that people are increasingly asking us about cloud computing. My tip: Do not save sensitive data outside your own area of control. Accordingly, companies should implement security solutions and dashboards on premise, and preferably not in the cloud.
Thank you for the interview.
Helge Sanden, Editor in Chief of IT-Onlinemagazin, asked the questions.

Ralf Kempf (CTO SAST SOLUTIONS)

Helge Sanden (Editor in Chief of IT-Onlinemagazin)
More articles about real-time monitoring:

