 At the DSAG Technology Days in Early May, the Vulnerability Management Working Group renewed its demand for a security dashboard, which SAP announced many years ago. In light of the current threat situation, it is advisable to stop waiting for it, particularly since good solutions from security specialists have become available in the interim, which also optimize the integration of SAP security with the overall enterprise security architecture. When it comes to end-to-end IT security, it is worthwhile to take a look at the operators of critical infrastructure (CIP) and the new German IT Security Act 2.0 (ITSA 2.0).
At the DSAG Technology Days in Early May, the Vulnerability Management Working Group renewed its demand for a security dashboard, which SAP announced many years ago. In light of the current threat situation, it is advisable to stop waiting for it, particularly since good solutions from security specialists have become available in the interim, which also optimize the integration of SAP security with the overall enterprise security architecture. When it comes to end-to-end IT security, it is worthwhile to take a look at the operators of critical infrastructure (CIP) and the new German IT Security Act 2.0 (ITSA 2.0).
According to a recent study by Bitkom, the umbrella organization of the German IT industry, published August 31, attacks on German companies cause damages of 203 billion euros annually. 84 percent of respondents were affected in the past year. “The threat that cyberattacks pose to the economy has become a focus of business and politics since the Russian invasion of Ukraine and its hybrid warfare in cyberspace at the latest,” said Bitkom President Achim Berg. 45 percent of companies believe that cyberattacks could threaten their commercial existence – a huge leap from nine percent in the previous year. In particular, operators of critical infrastructures have observed an increase in attacks: 87 percent of CIP companies surveyed say that attacks have increased somewhat to sharply. All the same, said Berg, the results from this year show that companies can take effective measures to defend against attacks or at least minimize the damage caused.
The IT Security Act 2.0
Government action is reflected in the new cybersecurity agenda of the German Federal Ministry of the Interior, which is primarily a declaration of intent to implement a strong security architecture, while the ITSA 2.0 that came into force this year for critical infrastructures is providing for facts on the ground. It demands procedural, directive, and reactive measures, such as security monitoring in systems and other monitoring measures to establish system hardening as a market standard. And there are specific requirements for designing the infrastructure and processes to be auditable, with biannual certification. This quality of the architecture and processes demands a rethink: Instead of continuing with business as usual, companies have to meet specific requirements. Responsibilities have been redefined and monitoring and control mechanisms must be integrated and enable real-time analysis.
Is SAP the weakest link?
SAP landscapes in particular show that the requirements of ITSA 2.0 are topical and are going in the right direction for non-CIP companies too, but understandably can’t cover all vulnerabilities. The requirements for SAP S/4HANA have changed once again, for instance: The database, user interface, gateway, applications, and authorizations have become more close-knit and access to important data has become more complex – and thus more difficult to monitor. ITSA 2.0 demands detailed business continuity planning and disaster recovery scenarios involving IDSes as “state of the art technology” (§ 8a). IDSes identify and substantiate attacks based on log files, which now have to be both recorded and analyzed. This will make SIEM systems indispensable for the rapid identification of cyberattacks in future, even though they usually do not suffice for SAP.
SAP is a world of its own
SIEM systems combine security information management (SIM) with security event management (SEM) to generate analyses of security alarms. Its key duties are to provide reports on security-relevant incidents and send notifications when an activity violates the predefined rule sets. The analyses use defined rules, correlation models, machine learning, and artificial intelligence to generate relations between the entries and identify anomalies. Unfortunately, this principle is hardly effective at all in SAP systems, because the specific SAP logs and analyses are not interpreted and, consequently, attack patterns are not identified or recognized. Classic SIEM tools consider IT infrastructures, not individual applications. Although it has become increasingly apparent in recent years that applications also have to be included – whether Microsoft Dynamics, a product planning tool, or an SPS in production – SAP is more of a network of its own, with its own roles and authorizations and its own security mechanisms, and also has its own nomenclature and rule sets.
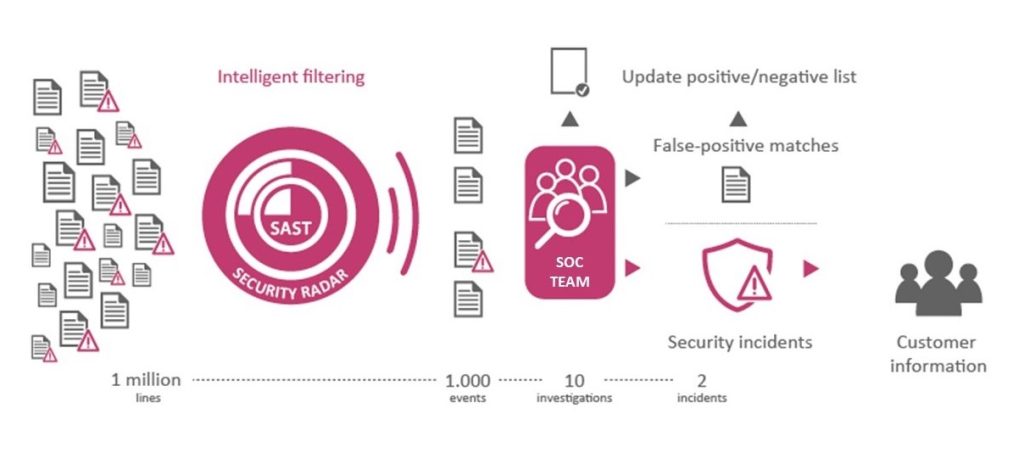
Integrating intelligent filtering
This lack of SIEM integration with SAP represents a significant, ongoing risk in the security architecture. This is where companies that use SAP software have to take action. According to the latest DSAG investment report 2022, four of five SAP customers already intend to invest in improving their cybersecurity. If no access to the SAP system is gained, SIEM can identify little more than a kind of ambient noise of logs with millions of entries. Exceptions in the SAP system may appear unremarkable at the network level. The only way to identify them is to consider the application itself. These communication problems often mean that SAP systems aren’t tackled seriously or are neglected – even at companies that have highly professional IT security, have deployed an SIEM system, and have excellent command of their non-SAP areas. Nonetheless, there are solutions to this critical security “blind spot”, because alternatives have become available to protect both worlds end-to-end.
Integration with SIEM
Specialized software tools can extract the events from the application layer and transport and translate them in a way that is comprehensible to SIEM network monitors. Detecting attacks based on log files and analyzing network traffic require in-depth knowledge of the potential paths and patterns that such incursions can follow. Events relevant to security have to be filtered out of a sea of data and placed in the proper context. Intelligent information management is necessary in order to assess security data of this kind and integrate it in the SIEM system. As such, effective tools for risk recognition not only analyze SAP logs, but also integrate configuration and role analyses, integrate this information from SAP systems in existing SIEM systems of all kind virtually out of the box, and enable their analysis. By integrating them with the SIEM tool, you can consolidate all the security-relevant incidents detected in your SAP systems with other areas of your IT landscape.
SAP security demands expertise
This is where the integrated dashboard described above plays a key role: It provides additional transparency for all systems – not only operators of critical infrastructure, but all companies with a realistic need for security, can get rated, visualized presentation and documentation of their overall security status at the touch of a button. As such, an immediate implementation of ITSA 2.0 for SAP requires the involvement of a professional security partner, both to effectively meet the requirements of Germany’s new IT Security Act 2.0 and at the same time to improve audit compliance of SAP system landscapes. The rollout of specialized software can help implement derivations of the template roles for the specific customer organization. In normal operations, it serves to validate roles and authorizations for security and SoD, analyze usage, further optimize roles and authorizations, and implement emergency user functions for support tasks of the IT employees. Under the perspective of ITSA 2.0, a pending SAP S/4HANA migration in particular provides an ideal opportunity to raise a company’s IT security to a new level. Legacy interfaces can be cleaned up and, above all, standardized – providing enormous security gains.
Dashboards: Visualization provides security
Companies often try to start with identifying vulnerabilities through automated processes. Recognition isn’t easy to learn, however, and often results in “overlearning” or incorrect learning, with the result that the algorithm fails to respond to actual threats. Instead, the top priority should be to automate and optimize the provisioning of information. By integrating an overarching SIEM tool, you can consolidate all the security-relevant incidents detected in your SAP S/4HANA systems with other areas of your IT landscape. This ensures that SAP is taken into account in SIEM and companies can generate a reliable depiction of their full security status in real time. Dedicated security dashboards offer a new level of transparency for the current security situation. In addition, the targeted expansion of knowledge for internal security efforts has one of the greatest impacts. After all, attack scenarios have to be truly understood in order to be managed effectively. Dashboards can clearly visualize results for security teams and enable them to identify changes to the threat situation and act upon them quickly.

Ralf Kempf, CTO, SAST SOLUTIONS and Vice President, ABAP Pathlock

This article was initially published (in German) in KES on September 16, 2022.
More about SIEM and Security Dashboards:

