 Despite the increasing use of web interfaces in the context of S/4HANA, batch processing is still required for mass data. However, our experience in customer projects has shown that very few administrators know how manage authorizations properly in such scenarios. SAP OSS Note 101146 offers a good overview in this regard. In this blog post, we want to provide a condensed explanation of how the practical aspects interrelate.
Despite the increasing use of web interfaces in the context of S/4HANA, batch processing is still required for mass data. However, our experience in customer projects has shown that very few administrators know how manage authorizations properly in such scenarios. SAP OSS Note 101146 offers a good overview in this regard. In this blog post, we want to provide a condensed explanation of how the practical aspects interrelate.
Batch processing: Who needs which authorizations?
In batch processing, we typically distinguish among several different scenarios:
| Scenario | Description |
| User self-service | A user wants to execute long-running programs once as a job. |
| Cyclical | Interface programs and cyclical reports are scheduled CENTRALLY (batch admin). |
| Batch user | The user (system user) utilized in a job step |
| Troubleshooter | For searching for errors |
| Batch input in batch mode | For processing sessions in a batch |
In the context of batch processing, the following authorization objects are relevant:
1. Object S_BTCH_JOB (job scheduling is NOT administrative, but local in the client)
A user who has no special authorization for jobs (that is, neither S_BTCH_JOB nor S_BTCH_ADM) can perform the following actions:
- Scheduling jobs of class C (this cannot be changed).
- Viewing and modifying steps in the user’s own jobs.
- Deleting the user’s own jobs.
- Viewing the details of the user’s own jobs.
Here, the problem is that a given job won’t start automatically; it has to be released by a batch administrator.
The actions supported by the object S_BTCH_JOB are explained below:
| Action | Description |
| PLAN | This action is irrelevant because jobs can be scheduled without any special authorization. However, since PLAN is subject to authority checks in some ABAP programs (when scheduling backups using DB13, for example), this value should always be present in batch authorizations. |
| DELE | Authorization to delete other users’ jobs. Users can delete their own jobs without special authorization. |
| LIST | Is not used. |
| RELE | Release authorization for the user’s own jobs. If the user has RELE authorization, jobs with a start date (immediate start, date/time, event trigger, etc.) are automatically set to “released” status upon being saved. If the user does not have RELE authorization, these jobs will remain set to “scheduled” status. Attempts to enter a start date will result in a “No release authorization” error. Other users’ jobs cannot be released. |
| SHOW | View the details, steps, and spool lists of other users’ jobs. When displaying steps, this only works without issue in 4.0A and later. Regardless of these batch authorizations, the user must have the necessary spool authorizations to display spool lists. The batch authorization SHOW only makes it possible to call up the spool request screen (SP01). |
| PROT | Authorization to display job logs. A user can either view the logs of all jobs or none at all. Here, no distinction is made between the user’s own jobs and others. Important: As of the support packages cited in Note 1672932, checks are no longer performed on this action. |
2. Object S_BTCH_ADM (batch administration authorization)
For more extensive job operations, authorization for the object S_BTCH_ADM must be available with a “Y” in the field BTCADMIN (which is the code ID for the batch administrator). This enables the user to perform all operations on any jobs across multiple clients.
In other words, S_BTCH_ADM with the value “Y” also includes the objects S_BTCH_JOB action*, S_BTCH_NAM and S_BTCH_NA1 with user/program = *. This authorization is therefore highly critical, as it makes it possible to change identities.
Due to the changes covered in Note 1702113, it is possible to put more precise restrictions on the authorization assignment using the object S_BTCH_ADM.
| BTCADMIN =Y | Batch super user with ALL authorizations. |
| BTCADMIN =N | Negates super user authorization; no authorization for advanced administrative tasks. |
| BTCADMIN =C | For copying other users’ jobs; see Note 1480677. |
| BTCADMIN =A or B | Optional additional check when creating class A or B jobs; see Note 1695812. |
| BTCADMIN =P | Special authorization for displaying jobs from other clients. |
Please note that a certain level of support package is required to use the values C, A, B, or P.
3. Object S_BTCH_NAM and S_BTCH_NA1 (utilization of other users in steps)
Another key authorization object for background processing is S_BTCH_NAM, which enables the user to execute the steps of a job as another user (cf. SM36 -> “Edit step”). To do so, a different name can be entered in the user field of a given step.
This requires the following:
- The job scheduler must have an authorization that contains the step user’s name for the object S_BTCH_NAM.
- The step user must exist in the same client as the job scheduler.
In 4.6C and later: The step user must be of the dialog, service, system, or communication type.
Release 7.52 (and later) contains the authorization object S_BTCH_NA1, which also checks program names AND user names.
Remember: S_BTCH_NA1 is always checked before S_BTCH_NAM!
Starting programs in batches
As of SAP release 2.x, the object S_PROGRAM checks the field TRDIR-SECU – that is, the authorization group of the program at hand.
As of release 7.40, you also have the option to activate checking for the object S_PROGNAM. Note 2272827 provides further information and instructions on this subject. The check for S_PROGNAM MUST first be activated in the customer’s system. Before doing so, however, be sure to set authorizations properly for S_PROGNAM; otherwise, NO ONE but the emergency users will be able to start any report or report transaction after the SACF scenario is activated.
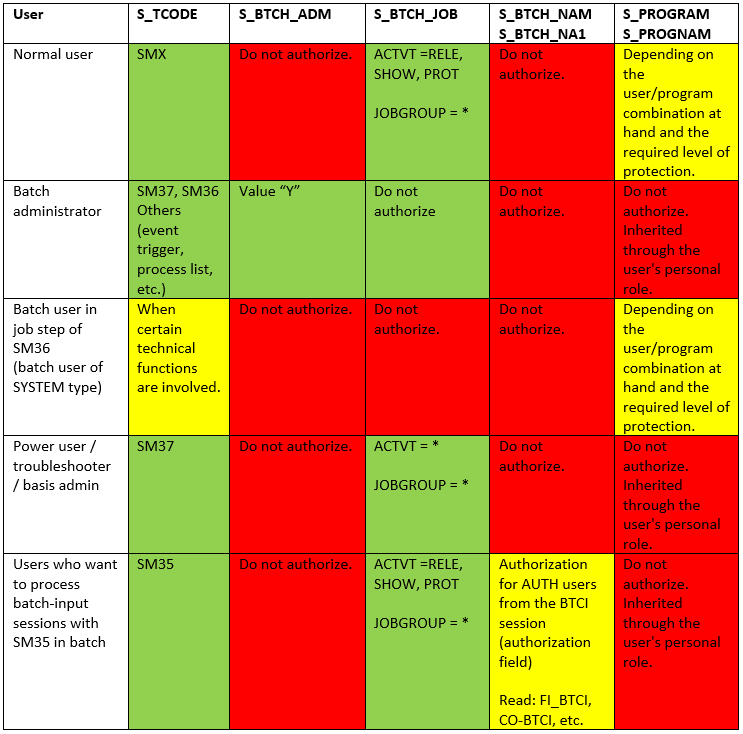
Overview for authorization assignment
For practice, the following authorizations should be assigned:
Do you have questions on this topic? Or are you interested in further information about our portfolio? We invite you to explore our SAST SOLUTIONS website or contact us directly: sast@akquinet.de

Ralf Kempf, CTO SAST SOLUTIONS
This might also be of interest to you
How can I quickly migrate SAP custom code to S/4HANA?
Cut Down on Critical SAP Authorizations Without Interrupting Operations.

