 Companies that operate SAP systems are subject to an annual audit by an auditor. Often, SAP authorizations are also examined. The audits check for separation of duties (SoD) and critical authorizations, in particular where SAP Basis Administration is concerned. Read this blog to learn how you can quickly reduce critical SAP authorizations (auditor findings).
Companies that operate SAP systems are subject to an annual audit by an auditor. Often, SAP authorizations are also examined. The audits check for separation of duties (SoD) and critical authorizations, in particular where SAP Basis Administration is concerned. Read this blog to learn how you can quickly reduce critical SAP authorizations (auditor findings).
Authorization objects and transactions in the context of SAP Basis are used in particular by business functions, and not infrequently. Some examples of these objects include:
- S_RFC (Remote Function Call)
- S_DATASET (access to files in application server directories)
- S_ADMI_FCD (various functions in SAP Basis Administration)
- S_SPO_ACT (actions related to the spool)
- S_TABU_DIS / S_TABU_NAM (access to tables)
- S_USER_GRP (maintenance of user masters)
- S_USER_AGR (maintenance of authorization roles)
- S_DEVELOP (ABAP development)
Of course, there are many more objects that could be added to this list. Critical transactions in the context of SAP Basis are also often handled too permissively. Examples include SE16 (Table Display), SM30 (Table Maintenance), SQ01 (Query Management), SPRO (System Customizing) and SCC4 (Client Settings), among others.
High Risks are Associated with Authorizations that are Assigned Too Freely
Again and again, ignorance of the criticality is the reason that authorization objects are defined comprehensively and critical transactions too often assigned. As a result, those responsible face increased IT risk that can have far-reaching consequences. The loss of entire system clients is a real threat if the way in which critical transactions are used is unknown – clients can be deleted in SCC5 – not to mention that availability and confidentiality can no longer be guaranteed
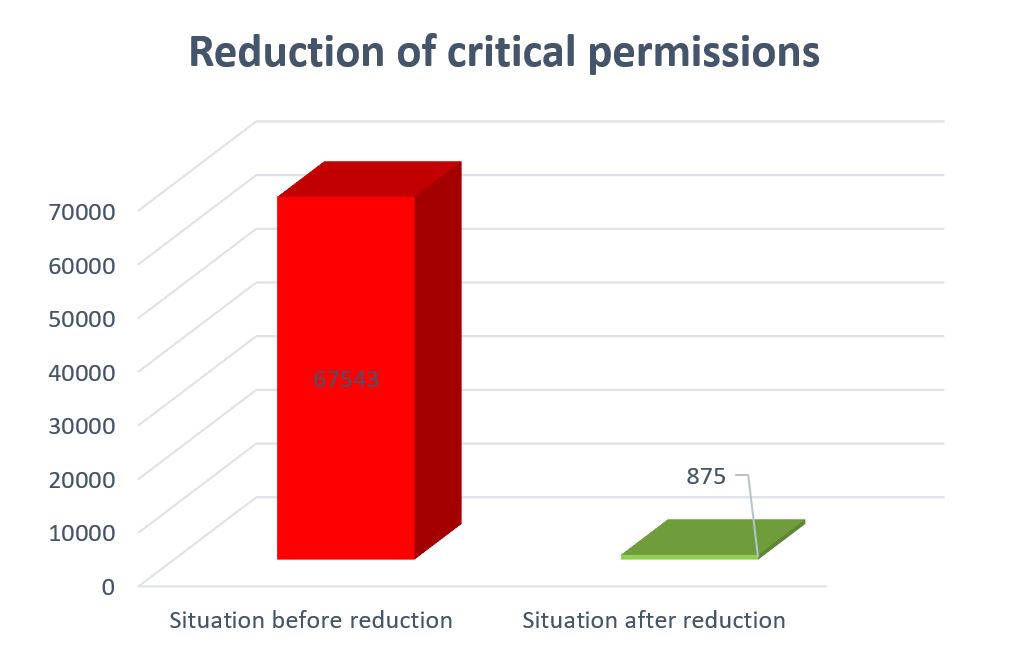
Quickly Reduce Critical SAP Authorizations (Auditor Findings)
Our GRC SAST SUITE allows some 95 percent of critical authorizations to be cleaned up. In addition, you can use it to easily analyze how critical object values are actually used across all users. The advantage of this is, in particular, that daily business is not affected at all.
Assigning authorizations based on our evaluations is easy and the people responsible are able to decide which users truly need them. Typically, users only rarely need this kind of critical authorizations, which is why removing them from the majority of users is possible without interrupting their work. Another objective is to separate authorizations according to the minimum principle. Not only will this help keep administrative expenses down, but it will enable you to meet today’s and tomorrow’s legal requirements.
Smooth Migration of SAP Authorizations
When you use SAST Go Live Management to go live, you are adding extra protections in the unlikely event of errors. One of the biggest challenges faced when migrating or redesigning SAP authorizations is ensuring the continuity of normal business operations. With our SAST Safe Go-Live Management approach, these problems are now a thing of the past.
Are you facing a similar challenge? Would you like to find out more about comprehensive protection of your SAP systems? Check out our SAST SOLUTIONS website or send us an e-mail to sast@akquinet.de.
We will be happy to advise you!

Steffen Maltig, Head of SAST Authorization Management for SAST SOLUTIONS
This might also be of interest to you
Handling Authorizations During an SAP Release Upgrade

