 In its S/4HANA release, SAP follows a strategy of process simplification and greater usability, among others. At the technical level, new layers such as the SAP Fiori Front-end Server, SAP Fiori launchpad, and SAP Fiori apps were created. The authorizations of these objects require particular attention to avoid nasty surprises as the project progresses. One specific pitfall is the changed file structure on the new application server.
In its S/4HANA release, SAP follows a strategy of process simplification and greater usability, among others. At the technical level, new layers such as the SAP Fiori Front-end Server, SAP Fiori launchpad, and SAP Fiori apps were created. The authorizations of these objects require particular attention to avoid nasty surprises as the project progresses. One specific pitfall is the changed file structure on the new application server.
In recent years, we have received many urgent inquiries from companies that initially thought they could handle the challenges of an SAP S/4HANA migration by themselves. Whether greenfield, brownfield, or bluefield approach, the problems they encountered nearly always followed a similar pattern: lack of experience with the technical migration to SAP S/4HANA. As a consequence, we have observed expensive extensions to the project timeline all too often.
In this first part of our blog series, we will show how the pitfalls caused by changes to the file structure can be thoroughly avoided.
How can you prevent negative side-effects caused by changes in the file structure of the new SAP S/4HANA application server?
SAP programs and customer developments that read and write data on the file system of the application server check the authorization object S_DATASET (authorization check for programs and files) or, alternatively, the object S_PATH (general checks for file access). Therefore, when you migrate technical roles from the ECC to a new SAP S/4HANA system, check the validity of the entries in the authorization object objects S_DATASET and the table SPTH.
The data structures on the new application structure are usually different, which can have negative side-effects on the migrated authorizations. When you modify the migrated roles, you prevent program terminations, since invalid values in authorizations inevitably cause a short dump. This is especially frustrating for test users, because they have to wait for the problem to be resolved before they can continue testing. System administrators also have to work harder to analyze and correct such problems. What’s more, the increased communication effort required for coordination shouldn’t be underestimated, because many programs can be affected, causing expensive delays to the overall process.
The remedy: Activating the authorization trace
We recommend activating the authorization trace as soon as your project starts, so you can begin building a knowledge base. Our SAST SUITE, with its extensive authorization trace, offers a helpful solution: You get a full overview of all object checks and can make targeted changes to roles quickly.
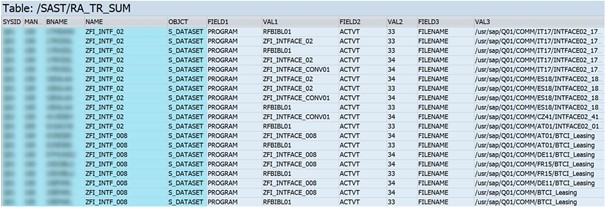
The information provided about object checks and effective filter options help you find out the situation quickly and derive the necessary activities. In addition to saving time and money, this also helps ensure the success of the overall project, which in turn increases the satisfaction of all stakeholders.
Don’t fall victim to the same pitfalls as other companies. We’ll be happy to advise you on your project and help you avoid nasty surprises. Visit our website or e-mail us.

Steffen Maltig (Head of SAP Consulting, SAST SOLUTIONS)
More articles on the topic:
Business partners and the sneaky back door of the F4 search help: How to protect your sensitive data

