 The lack of SAP security management dashboards is discussed often by the Security & Vulnerability Working Group at DSAG, the German-speaking SAP User Group. The Working Group sees such tools an essential prerequisite for developing and monitoring the improved security concepts that are urgently needed. Yet a majority of companies has yet to implement the dashboard technology although now would be a particularly good time to implement this efficient tool for mitigating attacks in light of the increasing threat level posed by malware and ransomware.
The lack of SAP security management dashboards is discussed often by the Security & Vulnerability Working Group at DSAG, the German-speaking SAP User Group. The Working Group sees such tools an essential prerequisite for developing and monitoring the improved security concepts that are urgently needed. Yet a majority of companies has yet to implement the dashboard technology although now would be a particularly good time to implement this efficient tool for mitigating attacks in light of the increasing threat level posed by malware and ransomware.
It is difficult for a security company like ourselves to understand this reluctance, because there are many benefits to using a security dashboard – for both effective, real-time monitoring and conserving internal IT resources. In the early stages, IT managers often want to achieve the greatest possible transparency and end-to-end monitoring in real time. Due to the particular complexity of the SAP systems in combination with many internal company needs, the implementation of a security dashboard demands detailed knowledge of the internal processes and responsibilities. Internal expertise is often insufficient in these areas. As SAP security experts, we are the ideal partner to compensate for these deficits.
Dashboard: a mere buzzword or a true help in meeting an enterprise’s day-to-day security needs?
We admit that the term “dashboard” is an overused buzzword. Many security tools that merely offer static monitoring in an attractive GUI call themselves “security dashboards”. The strength of a true security dashboard, however, is its ability to adapt to unforeseen developments, such as the current threat level.
A good security dashboard visualizes the information reflecting the diversity of the different systems and responsibilities for specific user groups, indicating deviations and enabling a top-down perspective of the security and compliance standard currently achieved.
Some SAP customers, for example, have to monitor the results of 2,000 individual check processes from 300 SAP systems daily in practice and identify both critical deviations in configuration and authorizations and potential attacks on the systems. The SAST SUITE enables you to do all this simply and in real time. Its dashboard lets you navigate through the different levels down to the details of a specific alert notification.
Enterprises have lofty expectations
Enterprises need a security monitoring and analysis solution that gives them a high level of transparency with the lowest possible implementation effort. They expect a security dashboard to support forensic analyses as well. What’s more, the solution not only has to show them where such problems exist, but also provide recommendations for eliminating them.
Success factors: system flexibility and simplified display
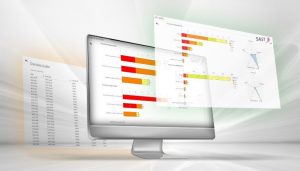 A modern security dashboard should enable you to consolidate the data for a given situation, regardless of which area. In addition, the dashboards must provide reporting for both the IT security department and for the system owners. System owners, in particular, need a simple overview with just two status values at the top level: one for the “configuration and authorizations” area and the other for “SIEM/real-time monitoring”. The system owners then know immediately where they need to take action and can get specific recommendations by clicking the area in question – all in real time.
A modern security dashboard should enable you to consolidate the data for a given situation, regardless of which area. In addition, the dashboards must provide reporting for both the IT security department and for the system owners. System owners, in particular, need a simple overview with just two status values at the top level: one for the “configuration and authorizations” area and the other for “SIEM/real-time monitoring”. The system owners then know immediately where they need to take action and can get specific recommendations by clicking the area in question – all in real time.
The results are impressive: real-time response to threats and conservation of internal resources
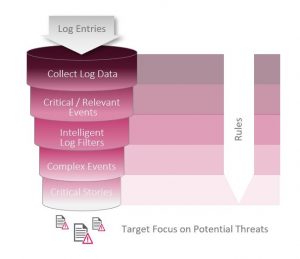
A security dashboard that has been tailored to your enterprise’s specific needs delivers two decisive benefits in day-to-day use: firstly, the possibility to react to critical situations in real time, and secondly the conservation of internal resources. Practice shows that customers can monitor several hundred SAP systems with just a few employees, worldwide and in real time, when they use an effective dashboard like the one provided in the SAST SUITE.
Benefits of a security dashboard for your SAP systems:
- High-quality information at the touch of a button
- Identification of vulnerabilities using an intuitive user interface
- Information on the causes of identified vulnerabilities
- Option to display all data – from aggregated risk key figures down to the detailed level
- Option to display trends over time
- Save IT department resources
Would you like to find out more? Visit our SAST SOLUTIONS website or just get in touch.

Ralf Kempf, CTO SAST SOLUTIONS
More articles on the topic:
The importance of reliably monitoring transactions in SAP systems
Rethinking real-time monitoring for IT security with the Internet of Things

