 SAP systems contain numerous transactions that enable applications to be accessed quickly. However, transactions can also be used to access sensitive business processes and confidential information. This is why events relevant to security have to be filtered out of a sea of data and placed in the proper context. This means that in order to evaluate and analyze conspicuous events, intelligent management is required.
SAP systems contain numerous transactions that enable applications to be accessed quickly. However, transactions can also be used to access sensitive business processes and confidential information. This is why events relevant to security have to be filtered out of a sea of data and placed in the proper context. This means that in order to evaluate and analyze conspicuous events, intelligent management is required.
Calling transactions in SAP systems – critical or not?
SAP systems contain numerous transactions that are used to activate SAP applications quickly in a single step. However, security-relevant areas can also often be accessed via transactions. This is why employees who are responsible for securing SAP systems have to ask themselves the following questions: Is even the mere calling of a transaction critical? Or does it only become relevant to security if a specific action is executed within the functions called?
Keeping a constant eye on your transactions and applications is therefore essential for the protection of your SAP ERP and S/4HANA environment.
Reduce your effort with tool-assisted monitoring.
A clear advantage of tool-assisted monitoring, such as the SAST Security Radar of the SAST SUITE, is that it comes with a comprehensive catalog of predefined critical actions (events in the SAP systems). Our SAST SUITE analyses this data for special features. You have the possibility of defining events individually via filter as well as when they should be triggered. This makes it easier for you to monitor critical actions in programs and functions reliably, because while a source is still reading data from the SAP system, it is analyzed and examined for special features.
When using critical actions in transactions, the DIALOG_TRANSACTION event is displayed, for example, whenever OK codes/buttons are triggered from the filter settings. This is also the case when the “RZ10” transaction is used. As a rule, every SAP Basis employee is authorized for this, since the call is often only used to view a specific parameter value of the configuration. As long as no change is made there, such behavior is therefore absolutely uncritical. However, you should take a closer look and be alerted if parameters are changed as well as saved. In order to ensure that only such calls are displayed, the function code is required.
Successfully monitor your transactions with the SAST Security Radar in just two steps.
In order to get a function code, first select the corresponding transaction. The example used here is RZ10. Using the menu, a double-click opens the “User interface status” field. This view shows the corresponding function code for each button:
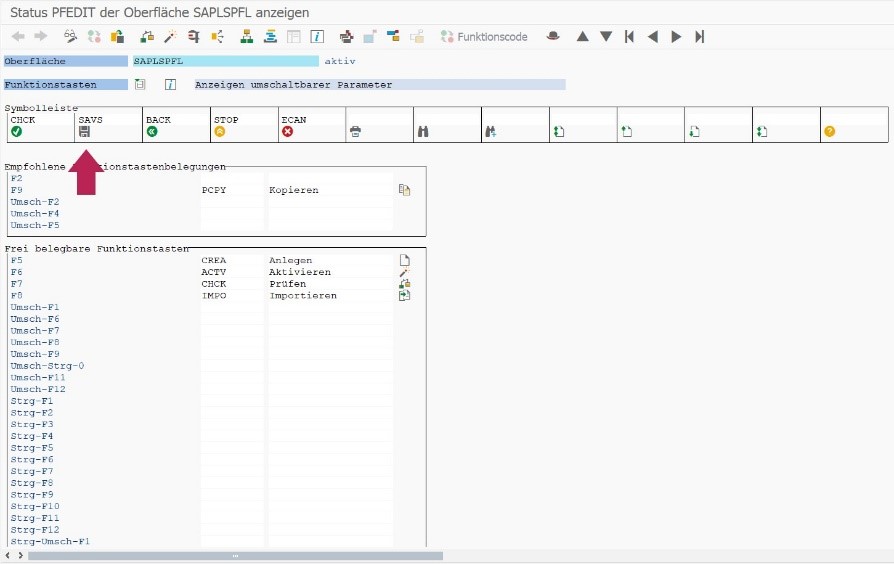
Figure: User interface status of transaction RZ10
Before you subsequently enter a transaction with the determined function code, first list all critical event calls with the possible function codes. You can then store the corresponding function code in change mode:
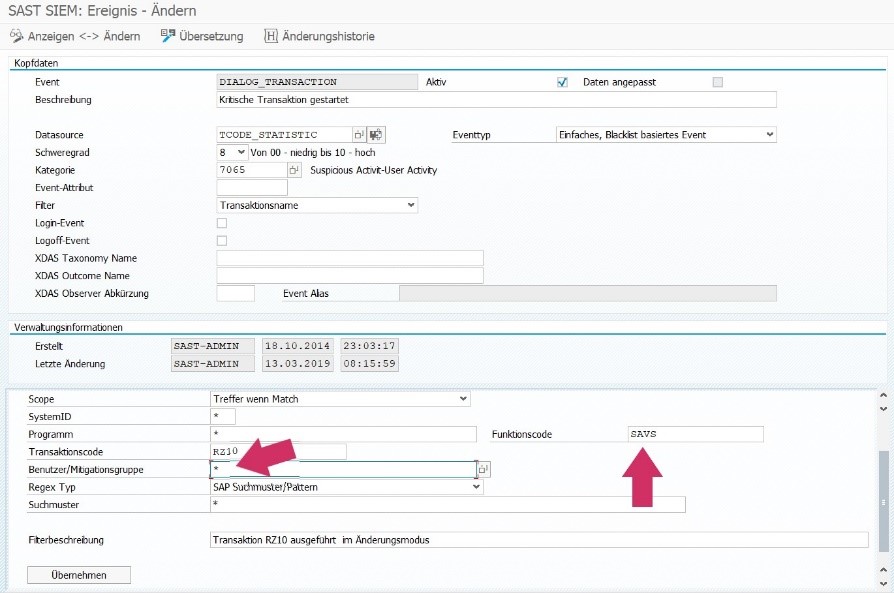
Figure: Definition of a DIALOG_TRANSACTION event for RZ10
This simple method enables the SAST Security Radar to reliably monitor critical transactions as well as execute critical actions in programs and functions.
Moreover, by integration with a comprehensive SIEM (Security Information and Events Monitoring) or SOAR (Security Orchestration, Automation and Response) tool, you can also consolidate all security-related event of your SAP ERP and S/4HANA systems with other relevant IT systems. The display of your security status will then be just a mouse-click away.
Would you also like to reliably analyze transaction activities, thereby protecting your SAP systems from attacks? Then please visit our website and feel free to contact us.

Viktor Vogt (SAP Security Consultant, SAST SOLUTIONS)
This might interest you too:
Study shows SAP systems especially prone o insider attacks
SAP home goes rogue – preventable attack vectors through the SAP GUI

