 Holistic, effective risk management in IT will help you make sounder decisions faster and present tremendous potential for value creation throughout your company. In practice, however, we continue to witness a lack of measures appropriate for identifying dangers early on. IT risk management is too often understood as a reactive process.
Holistic, effective risk management in IT will help you make sounder decisions faster and present tremendous potential for value creation throughout your company. In practice, however, we continue to witness a lack of measures appropriate for identifying dangers early on. IT risk management is too often understood as a reactive process.
Every company that deals in depth with risks in SAP authorizations must at some point make a decision on how to handle the corresponding security risks. As a rule, we can distinguish between three approaches:
- Reject risks and remove authorizations
- Reduce risks by taking corresponding actions
- Accept less severe risks that are less likely to arise
Effective risk and role management with SAST
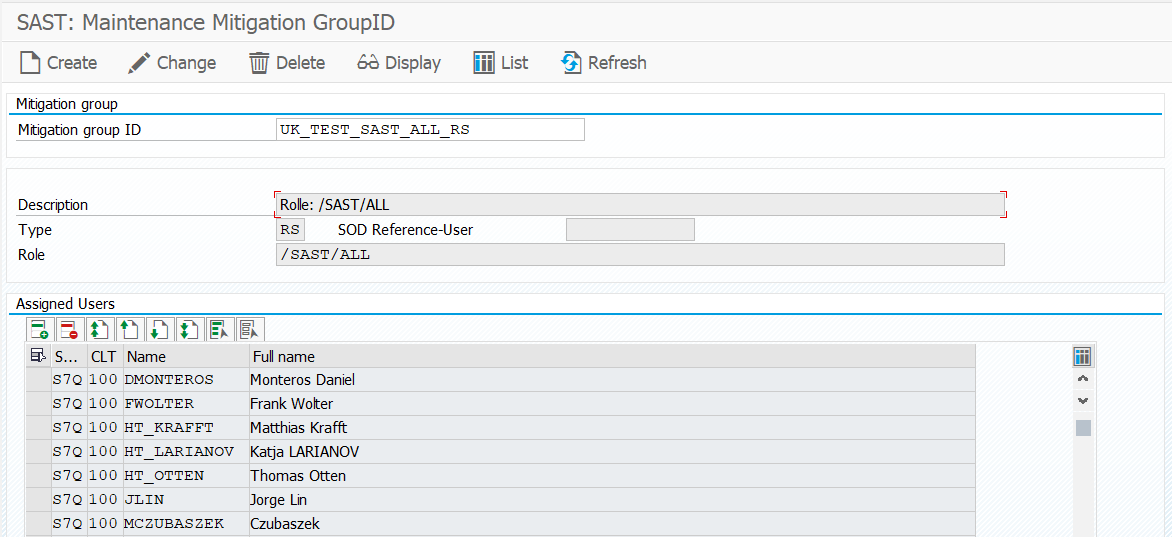
When specialists want to reduce risks, they talk about mitigation. Our GRC software, SAST SUITE, allows you to define any kind of mitigation decisions in the Risk & Compliance Management module. All you need to do is select the corresponding RiskID and UserID.
However, the time required to maintain individual decisions can add up quickly when you have a large number of users. This is what prompted the request to link mitigation decisions to the allocation of role authorizations. A user assigned a critical role as part of an acceptance process should then be documented within the corresponding mitigation decision in the system. The accepted authorization will then no longer be reported as a risk during risk evaluations. This is a big advantage because this step streamlines maintenance efforts as the system dynamically allocates roles for the mitigation entries.
The underlying principle behind dynamic mitigation groups has been implemented for both ABAP authorization roles and for business roles in connection with Identity Management (IDM).
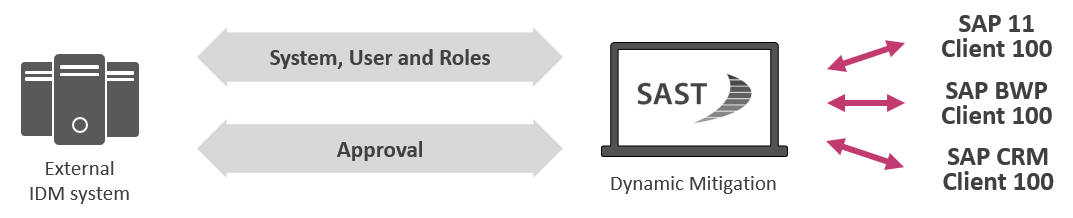
SAST SUITE risk evaluations classify the corresponding users automatically. This means that red flags are raised only for users who are assigned risky authorizations without the acceptance step. This greatly reduces time spent on risk analysis and provides maximum transparency.
Do you want to learn more about securing your SAP systems? Check out our SAST SOLUTIONS website or send us an e-mail us at sast@akquinet.de.


