 Almost all companies fine-tune their SAP systems with custom developments, but in doing so, they often expose themselves to severe security flaws. In particular, forgotten code that was only needed for a short time or has since been rendered obsolete by SAP’s own enhancements presents a further avenue for attacks.
Almost all companies fine-tune their SAP systems with custom developments, but in doing so, they often expose themselves to severe security flaws. In particular, forgotten code that was only needed for a short time or has since been rendered obsolete by SAP’s own enhancements presents a further avenue for attacks.
AKQUINET’s analyses show that up to 90% of ABAP code is no longer used. Frequently written for one-time situations and neglected ever since, such programming offers an ideal back door for hacking and other forms of manipulation.
Custom ABAP developments can lead to huge gaps in security
When it comes to code security, you’re sure to have heard arguments like these:
- The SAP standard ensures a secure APAB code.
- We safeguard our infrastructure and authorizations – that’s enough!
- Our internal code reviews are always conducted by at least two people.
- This sounds like a huge project that wouldn’t bring us any quantifiable return.
Don’t worry; you’re not alone. Plenty of companies have hesitated to audit their custom code and third-party add-ons, or have wound up dissatisfied due to the sheer number of findings such efforts produce. Meanwhile, developers tend to focus solely on functionality at the expense of security even though custom programming can entail significant security risks – especially in SAP environments. These vulnerabilities are easy to overlook, which is how they facilitate unauthorized access to both SAP and adjacent systems.
Is there a reliable way to assess the multitude of “critical” security flaws that can occur? And where do you even start to address them?
Unused ABAP code presents additional attack vectors
Perhaps we should start by busting the code security myths we listed above. Security is like an insurance policy: It costs less than undergoing a successful attack. Data security in particular is not a luxury, but an area that can quickly threaten a company’s existence if neglected.
Those who rely entirely on the SAP standard ignore the fact that among other limitations, it doesn’t apply to custom developments or add-ons. Plus, the free SAP Code Inspector only supports the simplest line-by-line checks. This offers no protection against insider manipulation, which is still the most common method of attack. Manual audits, meanwhile, require an inordinate amount of resources that are needed elsewhere.
It’s time for a tool capable of providing support that takes the pressure off of companies like yours in no time.
Shore up your ABAP code security with SAST
SAST Code Security Advisor (SAST CSA) identifies obsolete code and gives you a head start on safeguarding your latest developments, as well. This automated tool delivers prioritized findings that enable you to preserve your company’s resources. It checks your ABAP code for potential exploits and identifies complex vulnerabilities involving findings that seem benign on their own. This protects you from both data loss and fraud. In addition, SAST Code Security Advisor makes it easy to disable obsolete code. As we consistently see in the amount of unused code they contain, most SAP systems have grown gradually over time. This is why admins should first clean up their systems and deactivate unused programs as quickly as possible.
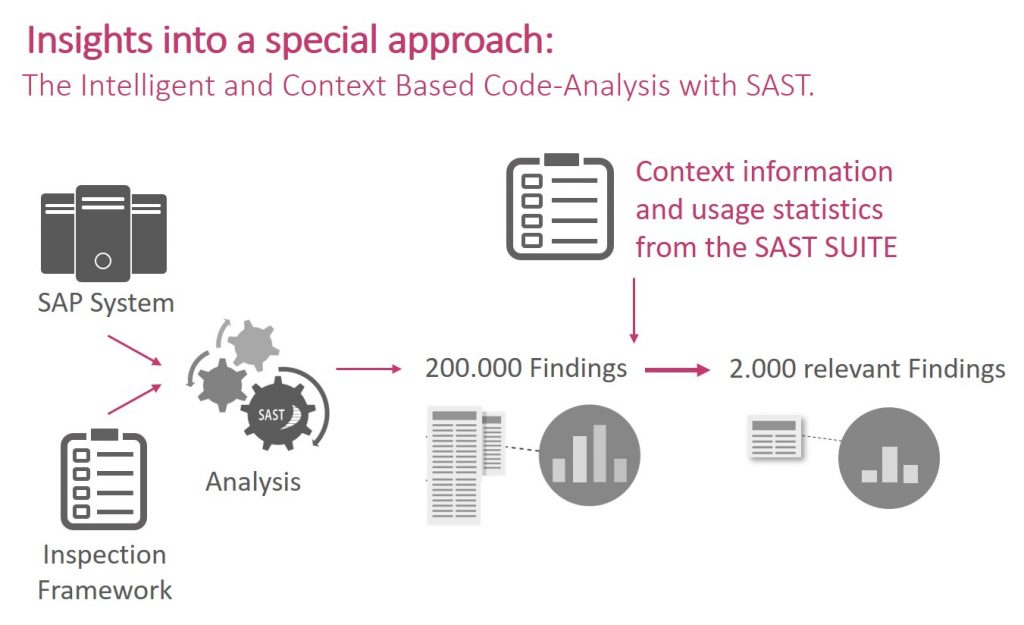
For identifying the most pressing security flaws, SAST Code Security Advisor includes a risk assessment component enhanced by key figures (such as user statistics), which is a key resource in prioritizing the issues that need to be addressed first. Instead of the hundreds of thousands of findings IT managers often receive, SAST provides an overview of those that are truly critical, along with specific recommendations from a predefined set of rules. SAP managers that already use a code scanner can combine it with this module as SAST CSA Cleansing to limit the number of false positives that occur, which will give their teams more resources to address the real problems.
When securing code, holistic planning is key
Companies that are working to eliminate the weaknesses in their ABAP code should bring their developers on board and train them accordingly. The resulting interactions often trigger learning processes that set the tone for the future. Since troubleshooting costs much less at the beginning than during live operations – or after a system failure – checking new developments for vulnerabilities can also save you a great deal of money.
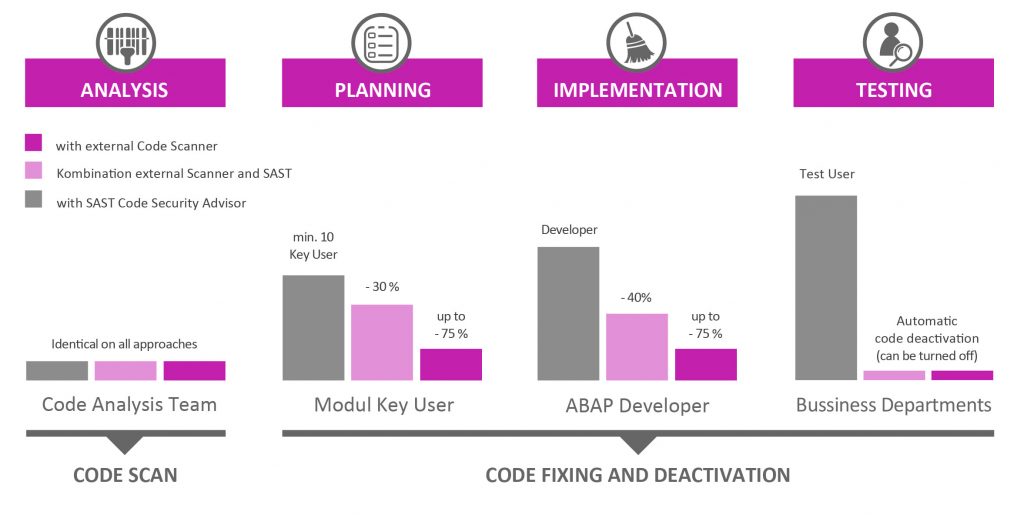
The advantages of SAST Code Security Advisor
- SAST CSA integrates directly into your SAP system, so your source code will never leave your company.
- Meaningful risk assessments will help you prioritize your troubleshooting efforts.
- Much fewer false positives will enable you concentrate on genuine weaknesses.
- SAST CSA identifies complex vulnerabilities involving findings that are not critical on their own.
- The tool will automatically deactivate your obsolete ABAP code and protect you from hidden back doors.
- It also provides meaningful notes and recommendations that will help you address findings.
- Available for licensing or as a managed service.
Do you want to learn more about securing your SAP systems with SAST Code Security Advisor? Check out our SAST SOLUTIONS website or send us an e-mail us at sast@akquinet.de.


