 Logical databases were once very popular. Complex selections were relatively easy to portray and effort-intensive reports were unnecessary. Users also appreciated the way dynamic selection worked, which encouraged developers to use the technique more and more. Starting from Version 7.50, SAP has now declared logical databases obsolete. Consequently, it advised against creating new logical databases, but allowed the old ones to continue as if nothing had happened. This, however, is a security risk that could impact any report.
Logical databases were once very popular. Complex selections were relatively easy to portray and effort-intensive reports were unnecessary. Users also appreciated the way dynamic selection worked, which encouraged developers to use the technique more and more. Starting from Version 7.50, SAP has now declared logical databases obsolete. Consequently, it advised against creating new logical databases, but allowed the old ones to continue as if nothing had happened. This, however, is a security risk that could impact any report.
To execute a report in an SAP system, the programmer’s code is enhanced by a number of internal instructions. For example, the “SPACE” constant is integrated via the <SYSINI> Include. In the context of logical databases, the subroutine two calls described in SAP help are likewise implemented (before_event and after_event). These subroutines are also built in – and executed in the case of a logical database.
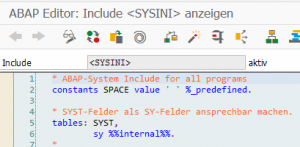
Within the built-in <SYSINI> Include is a statement that an attacker can exploit.
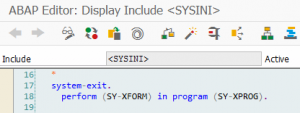
This statement is always filled with fixed (SAP Standard) reports in a normal report and is therefore noncritical. However, in the context of logical databases, the content of the SY-LDBPG variable is used to call standard routines. There is a distinction between how this field is filled by a “normal” generated report and by a report generated by a logical database.
Now, if it is possible to fill the field SY-LDBPG in a report without a logical database, for example via a user exit, then the subroutines known are called within the same program. Under normal circumstances, the subroutines are not implemented and there is no risk involved. However, the %_ROOT subroutine is called with the program of the system field. This allows a section of source code to be specified that is outside the control of the program.
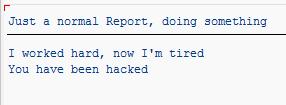
Example: This report without a logical database fills the field directly.
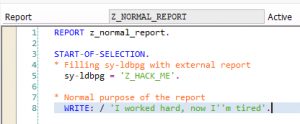
The only purpose of the report called was as a place to put the subroutine.
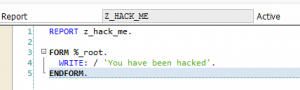
Result:
How to defend your ABAP code against attacks
The akquinet AG SAST Code Security Advisor allows you to recognize whether you have already fallen victim to this attack and to prevent it from happening again. You’ll only achieve a basic level of security that can weather stress tests and remain consistent if you take a truly head-to-toe approach to security. And that includes your ABAP code. The tool has a risk assessment enriched by key figures such as usage statistics to simplify prioritization for cleanup and an option to easily decommission obsolete code. This provides ideal protection from misuse of a potential backdoor.
Do you want to hear more about platform security? Has our SAST Code Security Advisor piqued your interest? Come visit our SAST SOLUTIONS website or contact us at knowhow@akquinet.de


