 Companies all over the world rely on SAP as their central enterprise software suite. That’s why it’s becoming ever more important for them to protect these SAP systems, along with the enterprise values they contain, with a professional cybersecurity and access governance strategy. Many international companies already trust the SAST SUITE to help them manage their international rollouts, and for good reason.
Companies all over the world rely on SAP as their central enterprise software suite. That’s why it’s becoming ever more important for them to protect these SAP systems, along with the enterprise values they contain, with a professional cybersecurity and access governance strategy. Many international companies already trust the SAST SUITE to help them manage their international rollouts, and for good reason.
Global deployment of the SAST SUITE – SAP security and authorization management in nine languages
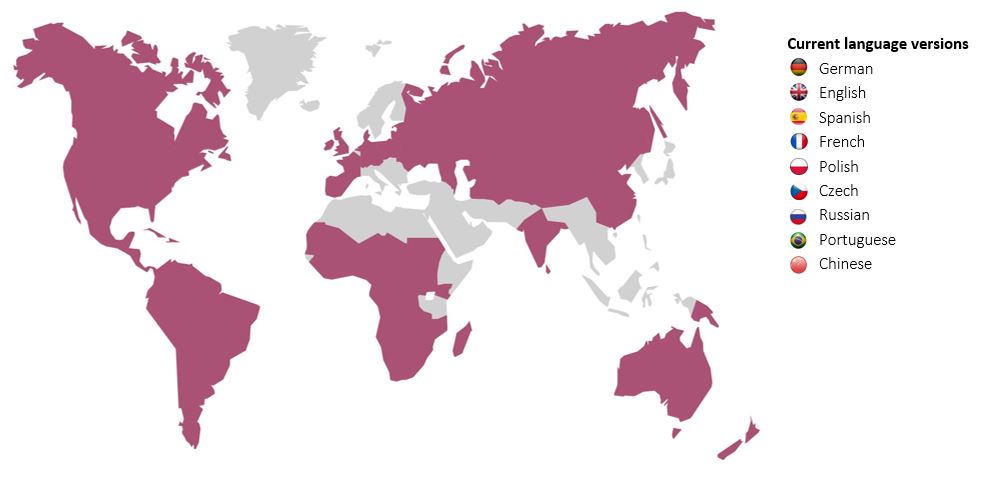
For nearly 15 years now, we have been rolling out the SAST SUITE software on nearly every continent. With this experience, we have succeeded in developing a project and rollout method for the SAST SUITE that guarantees a successful initiative for both cybersecurity and access governance.
A key prerequisite for this, first of all, involves finding out about the respective enterprise structure, to tailor the implementation and operating models to the individual situation at hand.
Four fundamental rollout risks must be observed in this process, while the complexity of the enterprise structure has a decisive influence on the success of global projects: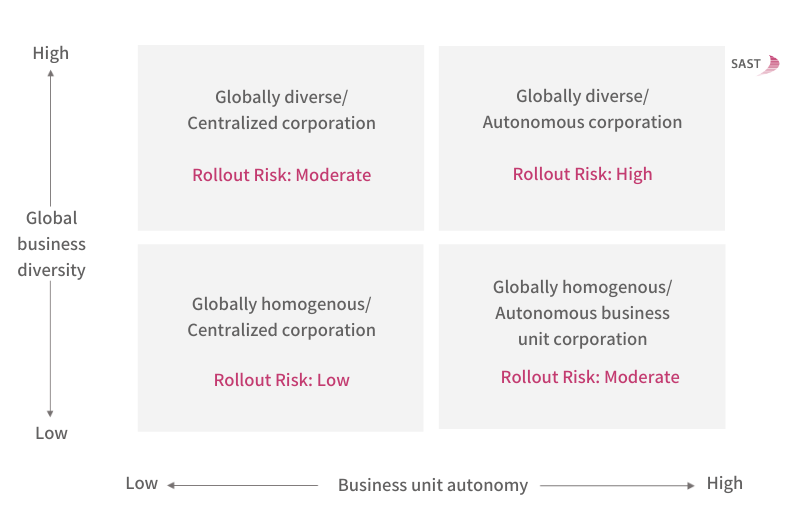
Nine success factors for a successful global rollout
Our tips for your rollout, derived from numerous successful projects:
- Develop a vision for your initiative, together with an operating model (for instance: centralized, decentralized, or hybrid)
- Define the project scope
- Get relevant stakeholders on board at an early stage
- Pay attention to local circumstances and cultural differences
- Define a global rule set and determine the degree of freedom that local organizations have to make modifications and enhancements
- Define a global project governance structure
- Set up a global rollout delivery team
- Develop a global rollout plan
- Coordinate the implementation phases for projects running in parallel
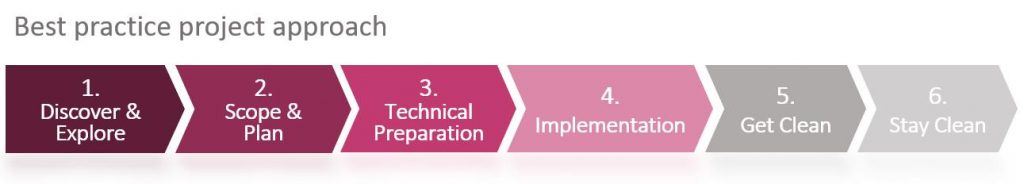
Phase 1 – Discover & Explore
The Discover & Explore phase starts with the onboarding of local stakeholders and the local project team in the project rollout. It also involves taking technical and functional inventory of the local SAP system architecture. During preparatory workshops, we familiarize the stakeholders with the functions of the SAST SUITE and develop a jointly coordinated project plan.
Phase 2 – Scope & Plan
In the Scope & Plan phase, we define the audit architecture together with the local unit. This phase also involves detailed planning of the implementation project, including clarifying the financial aspects.
Phase 3 – Technical Preparation
As the name implies, the preparations for implementing the SAST SUITE on the local SAP systems take place in the Technical Preparation phase. The basic installation and configuration work also take place here.
Phase 4 – Implementation
This phase involves the technical and functional implementation of the SAST SUITE on site. We implement the emergency user procedure in accordance with standards that are coordinated group-wide and also carry out an SAP Security & Authorization Check. This lets us determine the risk potential for your SAP landscape and identify potential attack vectors – in the infrastructure, SAP system parameters and module configuration, and in a review of authorizations and separation-of-duty risks. We present the results of this check to local management and, at the same time, incorporate them in the global risk database.
Phase 5 – Get Clean
Based on the risk potential identified in phase 4, during the Get Clean phase, we develop a remediation plan together with local management, to mitigate any SAP security and authorization-related risks and implement this plan reliably.
Phase 6 – Stay Clean
All the results and experiences from the previous steps are incorporated in the Stay Clean phase, which is based on coordinated measures in regular operations. This stabilizes the security status of your SAP landscape for the long term.
This rollout plan has proven to be highly successful in our SAST SUITE implementation projects, which we have carried out on four continents to date. Numerous companies trust our software solution, usually combined with our custom-tailored consulting services.
If you need support in the area of SAP cybersecurity and/or access governance – whether for national or international projects – we will be happy to provide our support. Visit our website or e-mail us.

Ansgar Rümpker (Principal SAP Consultant, SAST SOLUTIONS)
More relevant articles:
With the SAST SUITE again at the top of the KuppingerCole Leadership Compass
SAP Security & Compliance: “Customers need Solution Providers.”

