 The transition of the business world to SAP S/4HANA is picking up speed: that’s why every company should start preparing an end-to-end migration strategy for the new SAP system. It is essential that this strategy consider security aspects, as well, to avoid ending up sitting on millions in subsequent costs. The solution is Threat Intelligence.
The transition of the business world to SAP S/4HANA is picking up speed: that’s why every company should start preparing an end-to-end migration strategy for the new SAP system. It is essential that this strategy consider security aspects, as well, to avoid ending up sitting on millions in subsequent costs. The solution is Threat Intelligence.
“Significant unplanned costs can be incurred very quickly – firstly due to expensive follow-on measures when new vulnerabilities arise due to the migration or existing vulnerabilities that remained open, and secondly by a failure to clean up the source code during the migration process,” reports Ralf Kempf (CTO SAST SOLUTIONS).
We’ve identified the recent increase in cyberattack threat levels as a particular challenge. Faced with increasing system complexity, constant internal and external threats, and the pending changeover to SAP S/4HANA, companies have to pay special attention to SAP security in the current situation.
With a comprehensive security solution like the SAST SUITE, you can provide end-to-end coverage with real-time monitoring, to counter these current trends. “Our security audits show that every system is vulnerable,” explains Ralf Kempf. “But our strategy, a two-prong approach of consulting and software, can significantly reduce the probability of successful attacks – that means you’re making yourself a more time-consuming attack target, and if someone tries anyway, you can detect critical situations immediately and react without delay.”
How can companies confront the new threat level?
 We recommend a targeted approach, specifically one involving threat intelligence software with an early-warning system like the SAST SUITE. And to apply it end-to-end as part of a migration to SAP S/4HANA, we recommend an incremental procedure.
We recommend a targeted approach, specifically one involving threat intelligence software with an early-warning system like the SAST SUITE. And to apply it end-to-end as part of a migration to SAP S/4HANA, we recommend an incremental procedure.
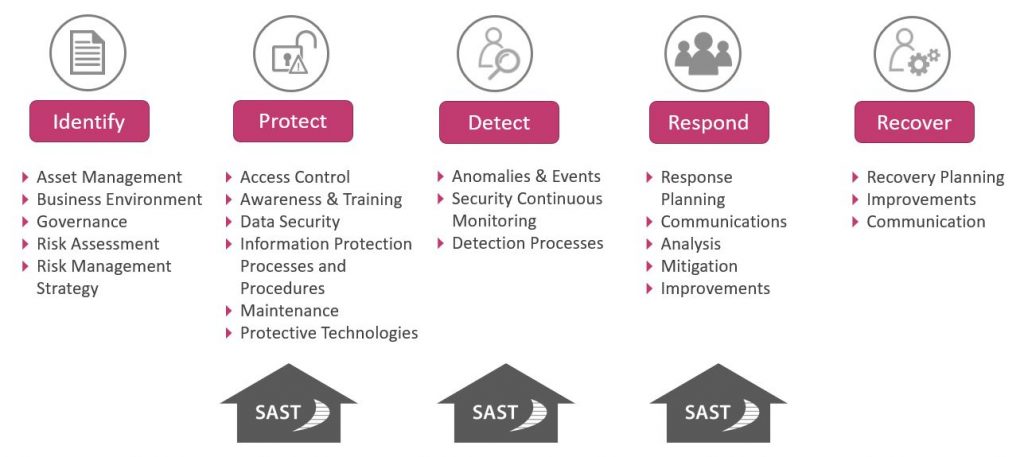
Threat detection in five steps: From identify to recover
1. Identify
- Identify vulnerabilities before the changeover to SAP S/4HANA
- Clear assignment of responsibilities
- Preparation and documentation of risk management
- An audit automation solution like the SAST SUITE to enable fast, qualified decisions
2. Protect
- Protect the systems
- System hardening in general and awareness training for employees
- The SAST SUITE serves as an additional tool to analyze and identify vulnerabilities at all levels and across all systems at the touch of a button
3. Detect
- Detect anomalies and attacks
- Continuous security management
- The SAST SUITE monitors the system constantly, analyzes log sources, detects threats by applying the matching patterns, and provides real-time notification
4. Respond
- Security Response, the answer to all threats to SAP systems
- Definition of responsibilities and reporting channels
- Execution of continuous analyses, to implement risk mitigation measures
- The SAST SUITE supports you here by recommending specific actions to remedy critical situation
5. Recover
- Recovery plan
- Learn from critical situations, implement improvements in the systems, and hone the communication and reporting channels
If you’d like to find out more about our threat intelligence solutions, follow our partner presentation “SAP Threat Intelligence: Optimal protection against cyberattacks.” at the DSAGLIVE event on October 14, 2020, or simply write us.

Ralf Kempf (CTO SAST SOLUTIONS)
Further posts on the topic:
SAP S/4HANA: How to ensure a secure S/4HANA migration
The most important elements of a cybersecurity strategy

