
On every second Tuesday of each month, SAP releases new Security Notes. Many SAP administrators install these patches relatively quickly – but are they putting too much faith in the security they provide?
Very few customers know that security gaps can still be exploited.
In OSS Note 1908870 – SACF | Workbench for Switchable Authorization Scenarios, SAP has developed a central solution for “switchable” authorization verification that makes it possible to conduct authorization checks for adapted functions only after they are activated by the customer. The idea is to reduce the effect on established authorization concepts.
Unfortunately, very few customers know that patches and enhancements designed in this way will remain inactive once this OSS Note is implemented. In other words, enhanced authorization checks that are meant to reduce risk can’t perform their intended function. The result? The corresponding security hole can still be exploited!
Compatible with customer-specific programs
With transaction SUCC, customers can also define scenarios for the custom programs they use. Scenario-based authorization checking enables developers to enhance standard software with alternative checks for authorization objects in a variety of use cases.
The use of switchable authorizations in customer-specific programs opens to door to intriguing possibilities with regard to developing and going live with ABAP modifications and authorization roles in separate environments.
Further information is available here.
Don’t forget – switchable authorizations need to be activated!
Transaction SACF enables you to activate predefined authorization checks that include authorization tracing and Security Audit Log integration.
For security reasons, customers are strongly advised to implement all the defined scenarios (except “SACF_DEMO_SCENARIO”) as live scenarios, as well. Here, auditors have to compare the amount of defined scenarios against the number of live scenarios and carry out rigorous evaluations.
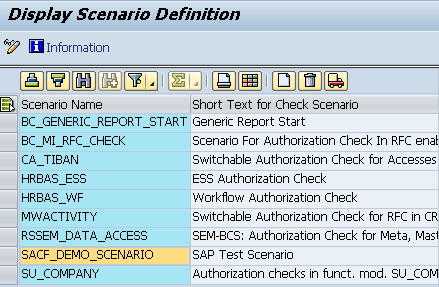
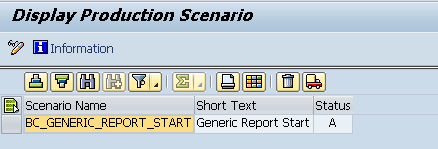
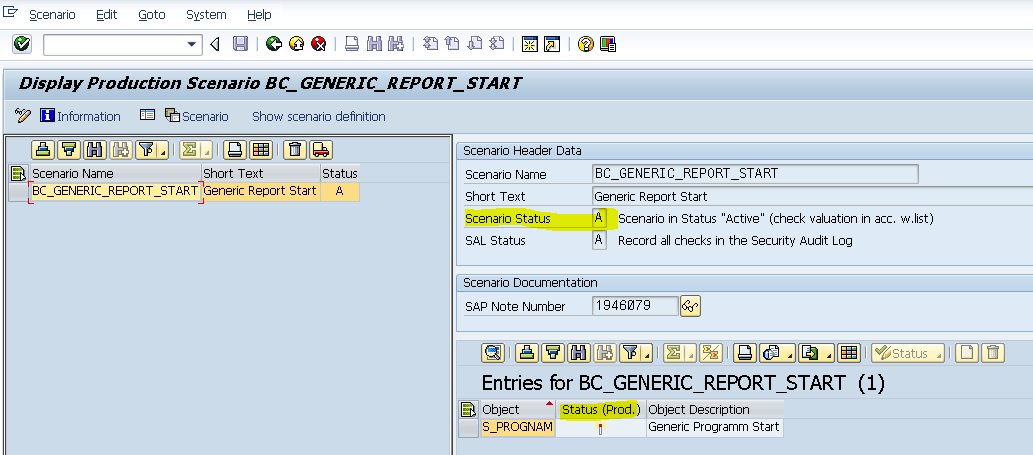
Once the defined scenarios go live, the system performs an authorization check, which activates enhanced protection.
Remember: Make sure that both header- and object-based verification are set to “ACTIVE”. Otherwise, the system may not carry out its checks (or only perform logging).
Required authorizations
In order to use scenario-based authorizations, you’ll need to assign your developers and admins corresponding privileges (S_TCODE).
Start with the authorization object “S_TCODE” and the following Transactions:
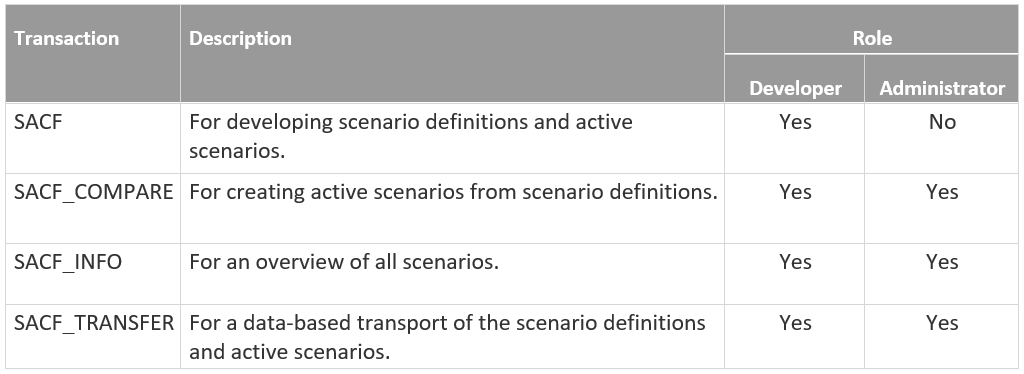
Then proceed to the authorization object “S_DEVELOP” and the corresponding object types (available activities: 02 for changes, 03 for display mode, and 06 for deletion).
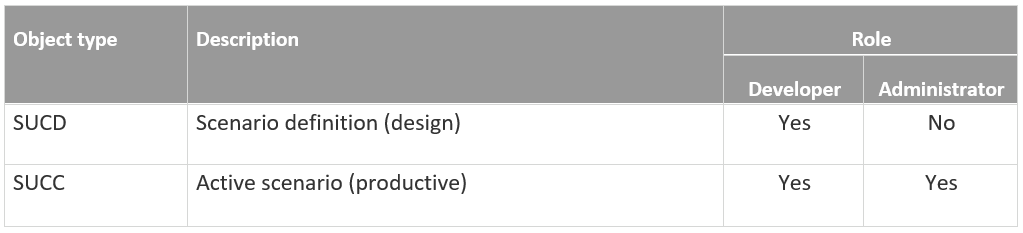
Remember: Don’t assign “change” or “delete” activities to users in live systems!

Ralf Kempf
Technical Managing Director for SAST SOLUTIONS at AKQUINET
Are you looking forward to further tips and recommendations in the field of SAP security and compliance? There are plenty of opportunities to engage with us – in one of our webinars, for example.

